After pawning the Forest.htb and Absolute.htb, I wanted to dive a little deeper into the Kerberos and the nature of attacking it. So I decided to write a blog series on Kerberos. The intention of this blog series is to provide a detail guide on What Kerberos means, How does it works? and Attacking on Kerberos. I will be referencing Massachusetts Institute of Technology’s Terminology page and couple of other Microsoft’s pages throughout this blog However, I will try to dive as deeper as possible to make it possible for you to understand certain basic concepts.
Key Concepts
- Kerberos Protocol: Kerberos is a network authentication protocol that helps two systems verify their identities when accessing resources. It relies on a trusted Key Distribution Center (KDC) to authenticate a user using a password. After verification, the system gives the user an access ticket to access resources through a Service Access Point.
- Mutual Authentication: Mutual Authentication is a security feature. While typical authentication proves the user’s identity to a server, Kerberos performs one extra step. It also ensures that the server you’re communicating with is genuine. This additional step helps prevent phishing and spoofing attacks.
- Principals:Kerberos creates distinct identities known as principals by combining a user’s username with their realm name, like “username@realm.name” (e.g., user.a@sale.com). Administrators utilize various principals to differentiate between regular and admin access. Administrators use multiple principals to distinguish between regular and admin access.
- Realms: Realms in Kerberos are the logical grouping of resources and identities. Your realm is a home of your identity and your point of entry to the network resource. In Windows, realm is also known as domain.
- Tickets: Kerberos uses tickets to keep password from being transferred in a clear-text and provide the ability to the users to sing in one time to access multiple resources. Once you provide a valid principal name and password, Kerberos issued you a tickets with a limited lifetime. This tickets allows you to access all the resources in the realm you belong to. Once the ticket is expired, a user would need to obtain another ticket. Tickets contain two encryption keys. The Ticket Key and the Session Key. The Ticket Key is shared between KDC and service you’re using. The session key is shared between user and the service and use to encrypt or decrypt the communication with the service. The Ticket Granting Service (TGS) is the ticket which user can use to authenticate against the service. It is encrypted with a Session key. The Ticket Granting Ticket (TGT) is the ticket presented to the KDC to obtain TGS. It is encrypted with Ticket Key.
- Agents: Couple of components works together in order to provide authentication in Kerberos. These are also known as agents. KDC, Application Server (AP), Authentication Service (AS), Client or users are the agents.
- Encryption Keys: There are several encryption keys used within Kerberos and these are encrypted to prevent tempering. These keys are as follows:
- Key Distribution Center (KDC) or krbtgt key: This key stores the NTLM hash for the krbtgt account. The krbtgt account is a default account in Active Directory, present in all domains. It serves as a service account for domain controllers when performing KDC operations. When a user authenticates with Kerberos, they receive a TGT (Ticket Granting Ticket) signed with a key derived from the krbtgt account’s password. This makes the krbtgt account crucial because knowing its password would allow an attacker to create arbitrary tickets, also known as Golden Tickets.
- User Key: A user key is NTLM hash derived from the user’s password.
- Service Key: Service key is NTLM hash of the service owner which can be a computer or user.
- Session Key: This is an important key as it negotiated between the user and KDC.
- Service Session Key: This key can be used between user and the service owner.
- Key Distribution Center (KDC) or krbtgt key: This key stores the NTLM hash for the krbtgt account. The krbtgt account is a default account in Active Directory, present in all domains. It serves as a service account for domain controllers when performing KDC operations. When a user authenticates with Kerberos, they receive a TGT (Ticket Granting Ticket) signed with a key derived from the krbtgt account’s password. This makes the krbtgt account crucial because knowing its password would allow an attacker to create arbitrary tickets, also known as Golden Tickets.
- Messages: The Kerberos authentication protocol uses a different kind of messages.
- KRB_AS_REQ: Request for TGT: A message requesting the Ticket Granting Ticket (TGT) from the Key Distribution Center (KDC).
- KRB_AS_REP: TGT Response: A message from the KDC containing the TGT, in response to the KRB_AS_REQ.
- KRB_TGS_REQ: Request for TGS: A message used to request the Ticket Granting Service (TGS) from the KDC, utilizing the TGT received earlier.
- KRB_TGS_REP: TGS Response: A message from the KDC containing the Ticket Granting Service (TGS), in response to the KRB_TGS_REQ.
- KRB_AP_REQ: User Identification: A message used to prove the user’s identity when requesting a service from the TGS.
- KRB_AP_REQ: Service Identification (optional): An optional message used by a service to verify its identity to the user.
- KRB_ERROR: Error Notification: A message indicating an error that occurred during the communication process.
- KRB_AS_REQ: Request for TGT: A message requesting the Ticket Granting Ticket (TGT) from the Key Distribution Center (KDC).
The following Image can explain the above messages in a diagram.
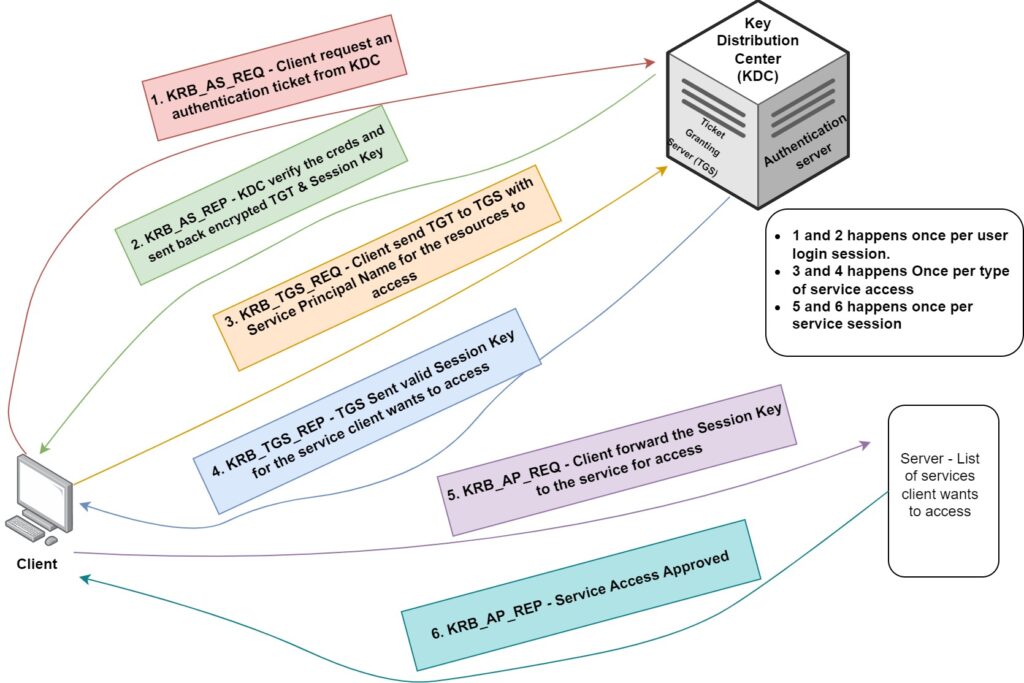
So now we’ve some basic understanding of certain Kerberos definations and how does this authentication protocol work. There are some attacking vectors that attached with this authentication prorocol and I am going to demonstrate all of those attacks in the next part of this blog series.
Stay tune!!
